really satisfying thing is that Murnane is a deeply elliptical writer so you could probably come across these preoccupations (detailed constructions of private games, horse racing) in dozens of his books
25) THE WEST PASSAGE by @vandroidhelsing.bsky.social. I would eat the mellified man, no question. An illustrated manuscript brought to life in a palace the size of a country. Exciting social gender constructions and deliciously surreal.
the interesting thing about studying the deep past is that the first major constructions (i.e. the first evidence of massive collective endeavors) were all devoted to (1) the dead as opposed to the living, (2) groups as opposed to individuals, and (3) non-functional (i.e. ceremonial) purposes
Pacmann: Efficient Private Approximate Nearest Neighbor Search (Mingxun Zhou, Elaine Shi, Giulia Fanti) ia.cr/2024/1600


Simplified PIR and CDS Protocols and Improved Linear Secret-Sharing Schemes (Bar Alon, Amos Beimel, Or Lasri) ia.cr/2024/1599


DeepFold: Efficient Multilinear Polynomial Commitment from Reed-Solomon Code and Its Application to Zero-knowledge Proofs (Yanpei Guo, Xuanming Liu, Kexi Huang, Wenjie Qu, Tianyang Tao, Jiaheng Zhang) ia.cr/2024/1595


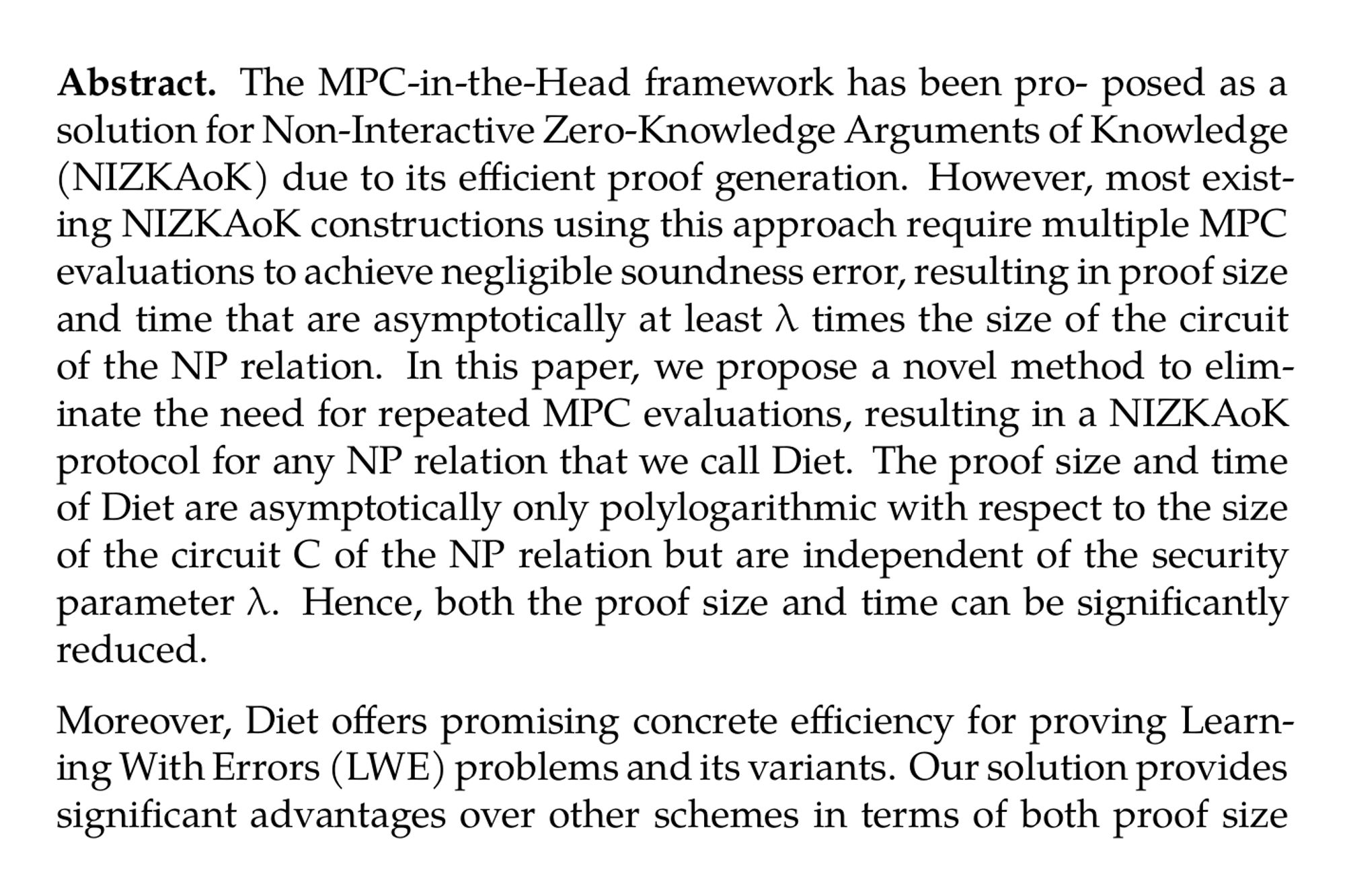
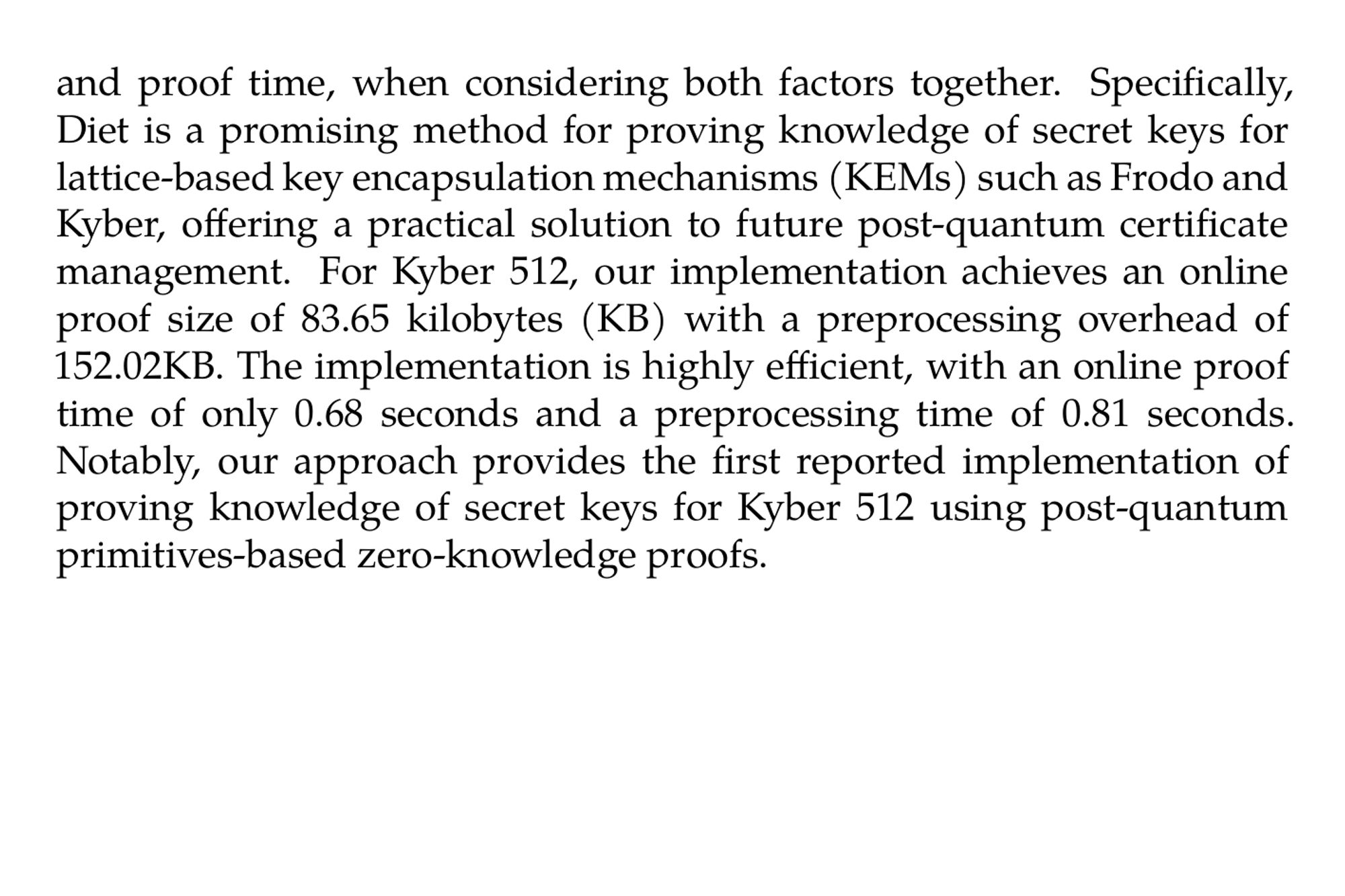
MPC-in-the-Head Framework without Repetition and its Applications to the Lattice-based Cryptography (Weihao Bai, Long Chen, Qianwen Gao, Zhenfeng Zhang) ia.cr/2024/1591
»A planetary configuration – two-thirds water, one-third land – changes the relationship between human constructions and natural entities« Giles, Negative Antipodes | #Seascapeshttps://buff.ly/4eFuaT3


