The database where the neurologs of the neuro-stimulator are recorded was encrypted to prevent unauthorized access and the code for decryption was also encrypted. Only employees with security level A have access to this data.
Passware Kit 2024 v4 introduces full support for macOS 15 Sequoia, enhanced GPU-accelerated password recovery, and a new hardware benchmark feature, offering improved usability and performance for password decryption and recovery tasks. #digitalforensics
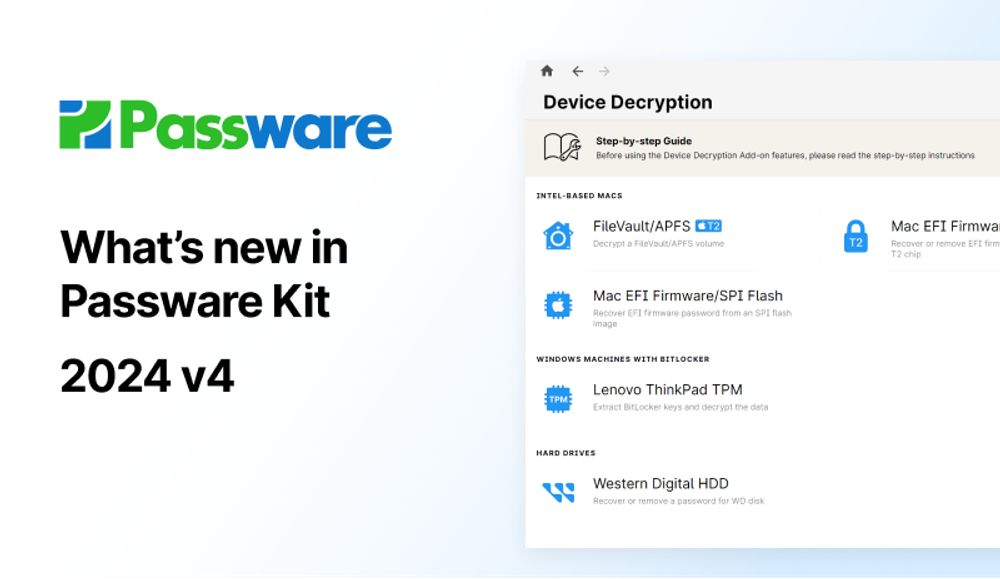
Passware Kit 2024 v4 introduces full support for macOS 15 Sequoia, enhanced GPU-accelerated password recovery, and a new hardware benchmark feature, offering improved usability and performance for password decryption and recovery tasks.
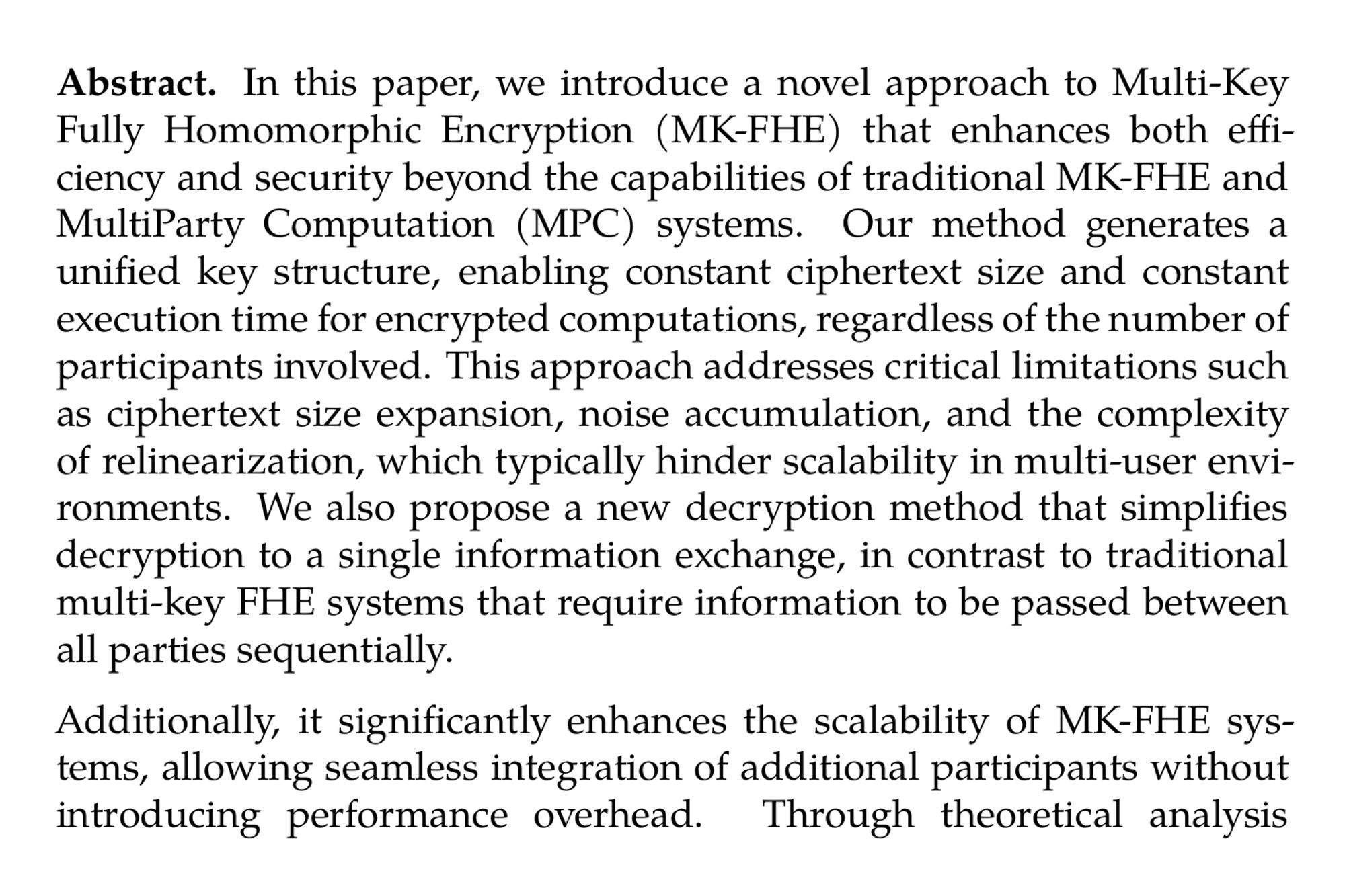
A New Approach Towards Encrypted Data Sharing and Computation: Enhancing Efficiency Beyond MPC and Multi-Key FHE (Anil Kumar Pradhan) ia.cr/2024/1622

Shaking up authenticated encryption (Joan Daemen, Seth Hoffert, Silvia Mella, Gilles Van Assche, Ronny Van Keer) ia.cr/2024/1618


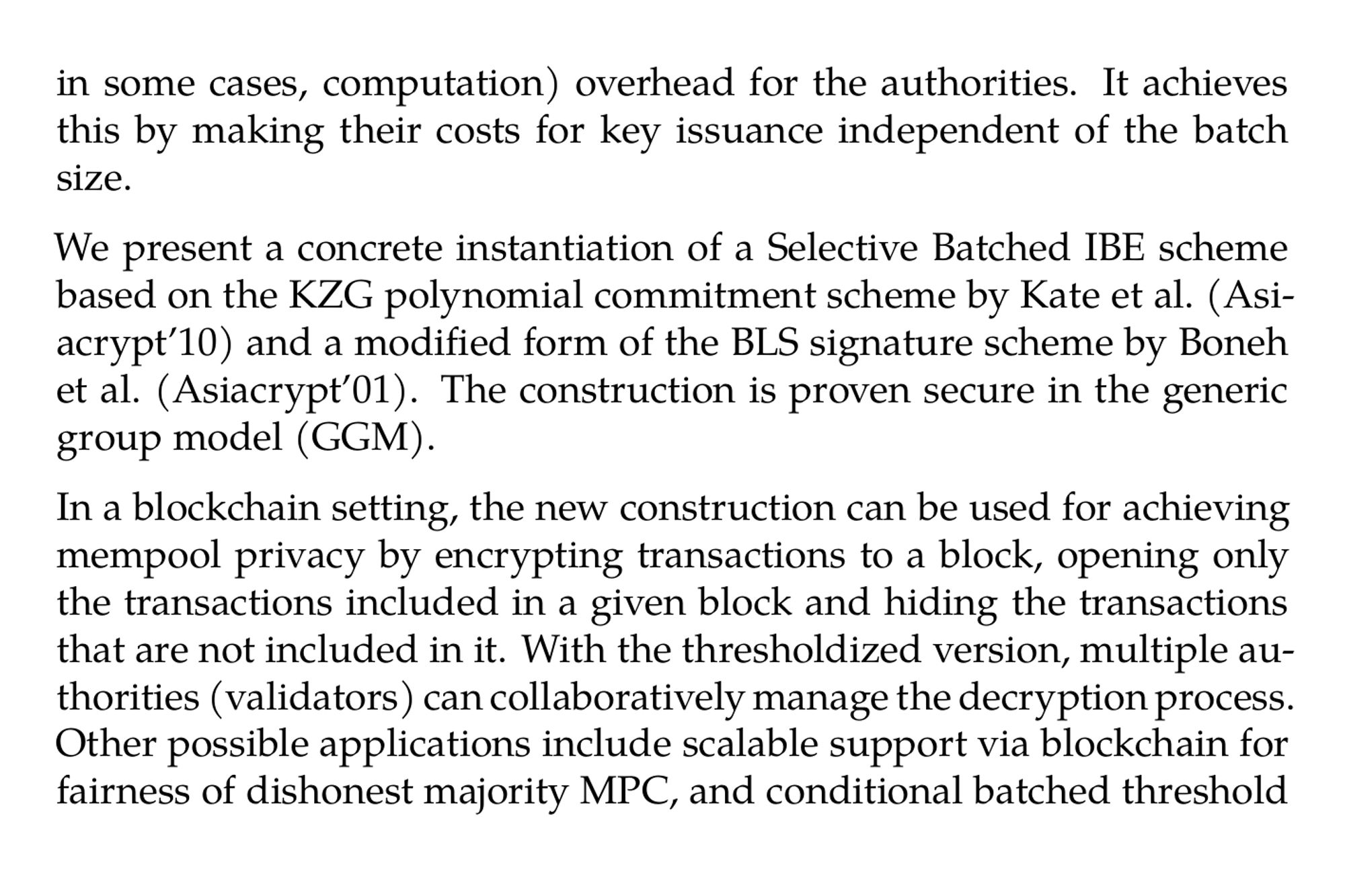
Efficiently-Thresholdizable Selective Batched Identity Based Encryption, with Applications (Amit Agarwal, Rex Fernando, Benny Pinkas) ia.cr/2024/1575


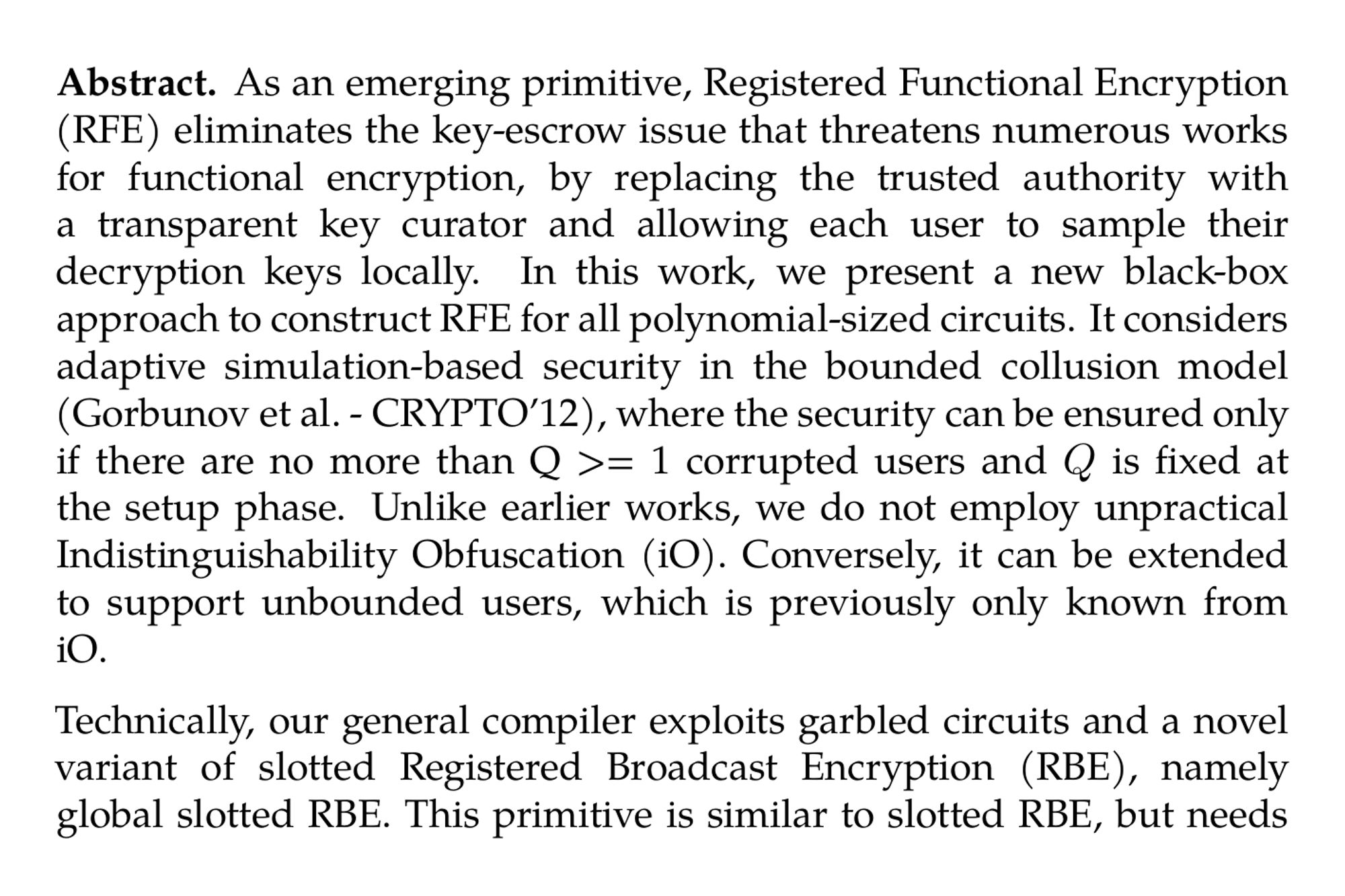
Bounded Collusion-Resistant Registered Functional Encryption for Circuits (Yijian Zhang, Jie Chen, Debiao He, Yuqing Zhang) ia.cr/2024/1572

BEAT-MEV: Epochless Approach to Batched Threshold Encryption for MEV Prevention (Jan Bormet, Sebastian Faust, Hussien Othman, Ziyan Qu) ia.cr/2024/1533

Moth Code The "Moth" has encrypted the information that was sent back. You must find the decryption key to unlock and decipher it. Based on the number of intel pieces gathered during the investigation, corresponding rewards can be unlocked.

The Netherlands will oppose a proposal in the EU that would demand decryption of private communication to detect CSAM. An unexpected critic of the idea is the Dutch Intelligence agency AIVD that warns of the risk to national security. www.bitsoffreedom.nl/2024/10/01/s...#digitalrights#lawsky

