Congrats! I love to read 💖 What sort of stuff are you in to? I'm reading a really fun cozy mystery series right now if that's your jam; just finished book 7. www.amazon.com/Eastwind-Wit...

Check out the online portal for "EastWind Books" one of the US only AAPI owned bookstores www.asiabookcenter.com#aapi#independentbookstore

LOCAL INDEPENDENT BOOKSTORE SELLING ASIAN AMERICAN, LANGUAGE LEARNING, CHINESE MANDARIN, MARTIAL ARTS, TRADITIONAL CHINESE MEDICINE BOOKS, QIGONG BOOKS, ART SUPPLIES, CHINESE PHILOSOPHY, EASTERN RELIG...
The Eastwind flew faster still (from The Garden of Paradise) https://www.wikiart.org/en/edmund-dulac/the-eastwind-flew-faster-still-from-the-garden-of-paradise

EastWind campaign targets Russian organizations with sophisticated backdoors https://buff.ly/4cpKW73
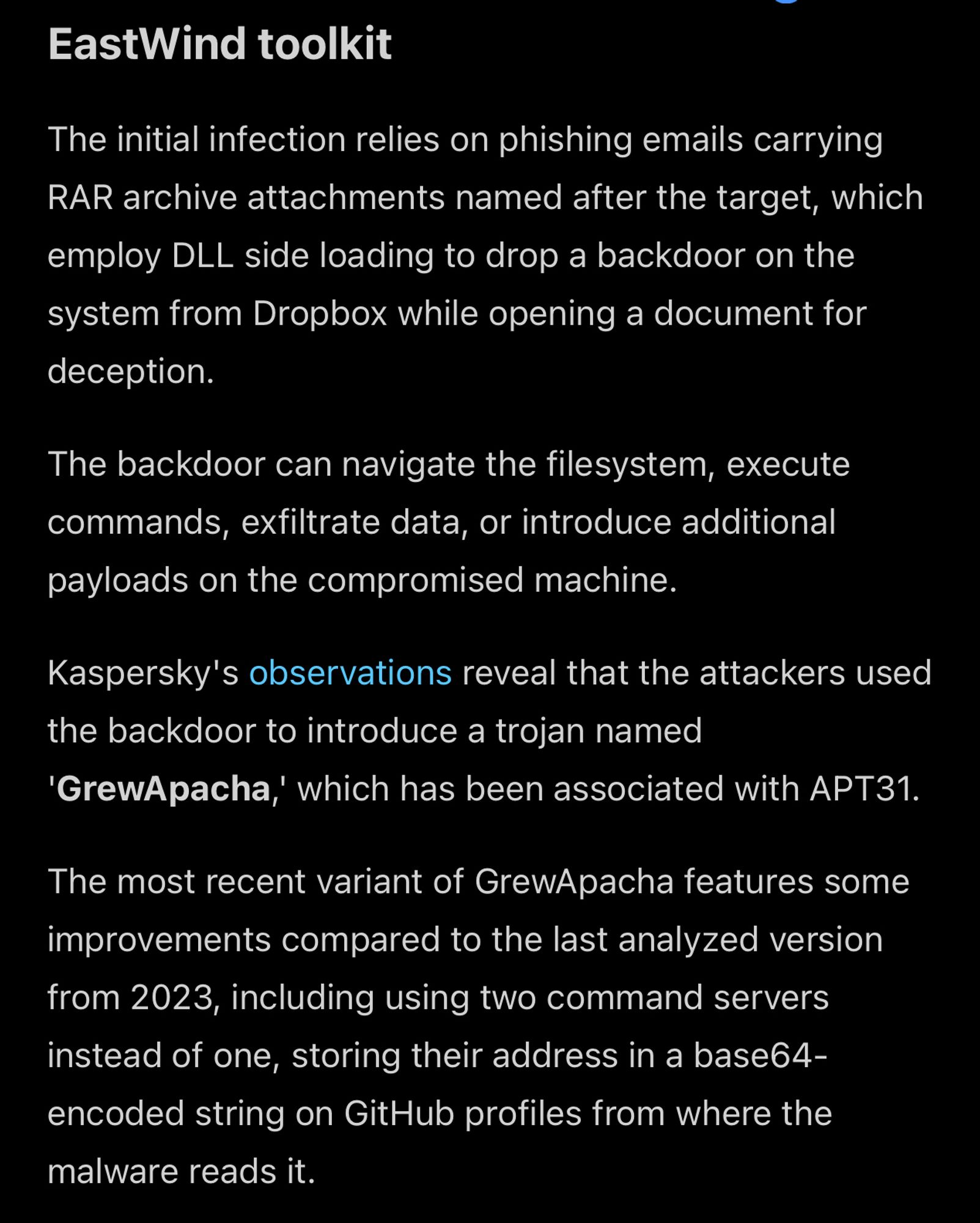
A campaign tracked as EastWind is targeting Russian government and IT organizations with PlugY and GrewApacha Backdoors.
卡賓斯基報告,國際知名的中國黑客團隊APT27、APT31對俄羅斯政府展開間諜攻擊 媒體報導 www.theregister.com/2024/08/15/s...securelist.ru/eastwind-apt...
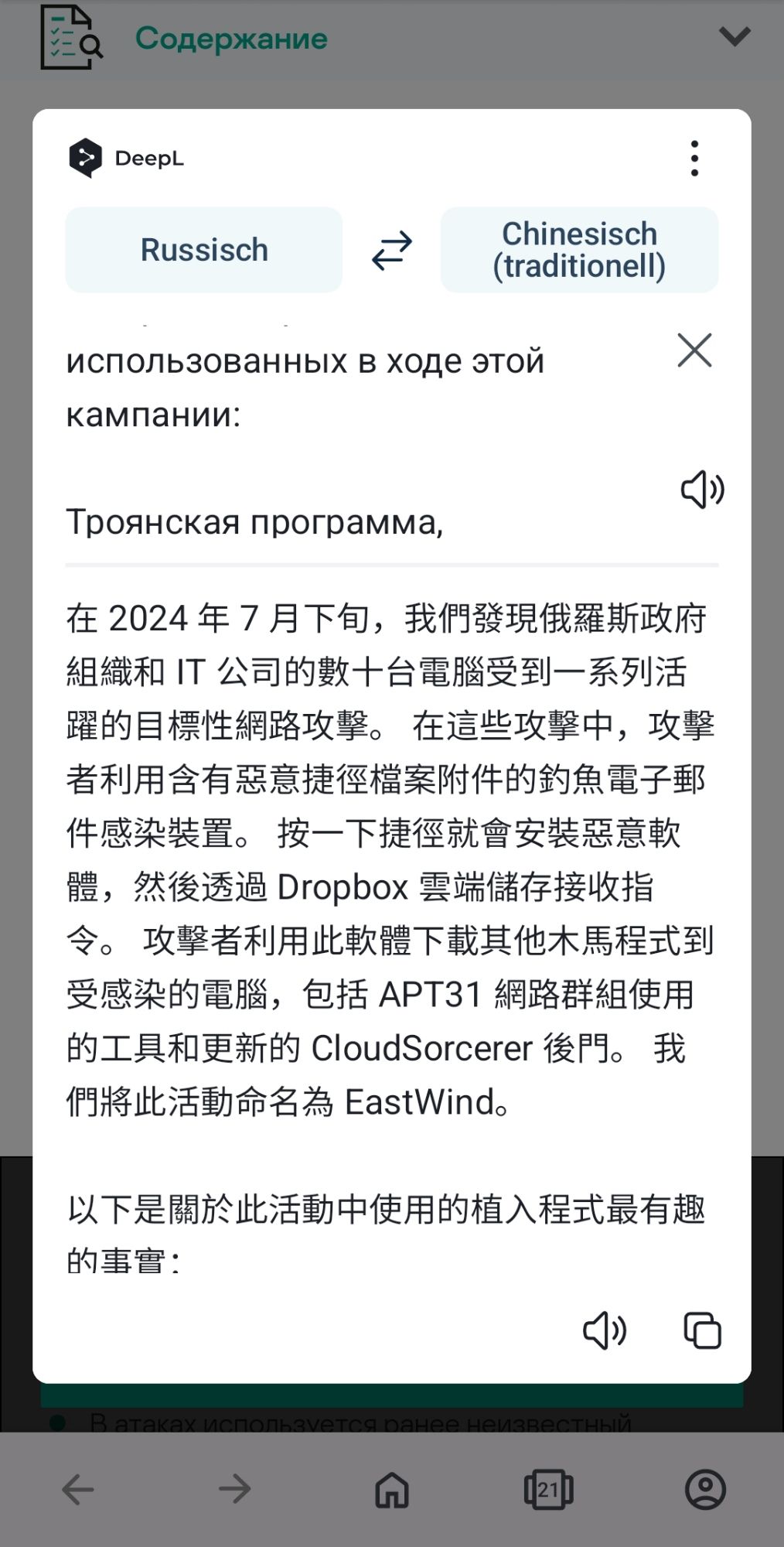
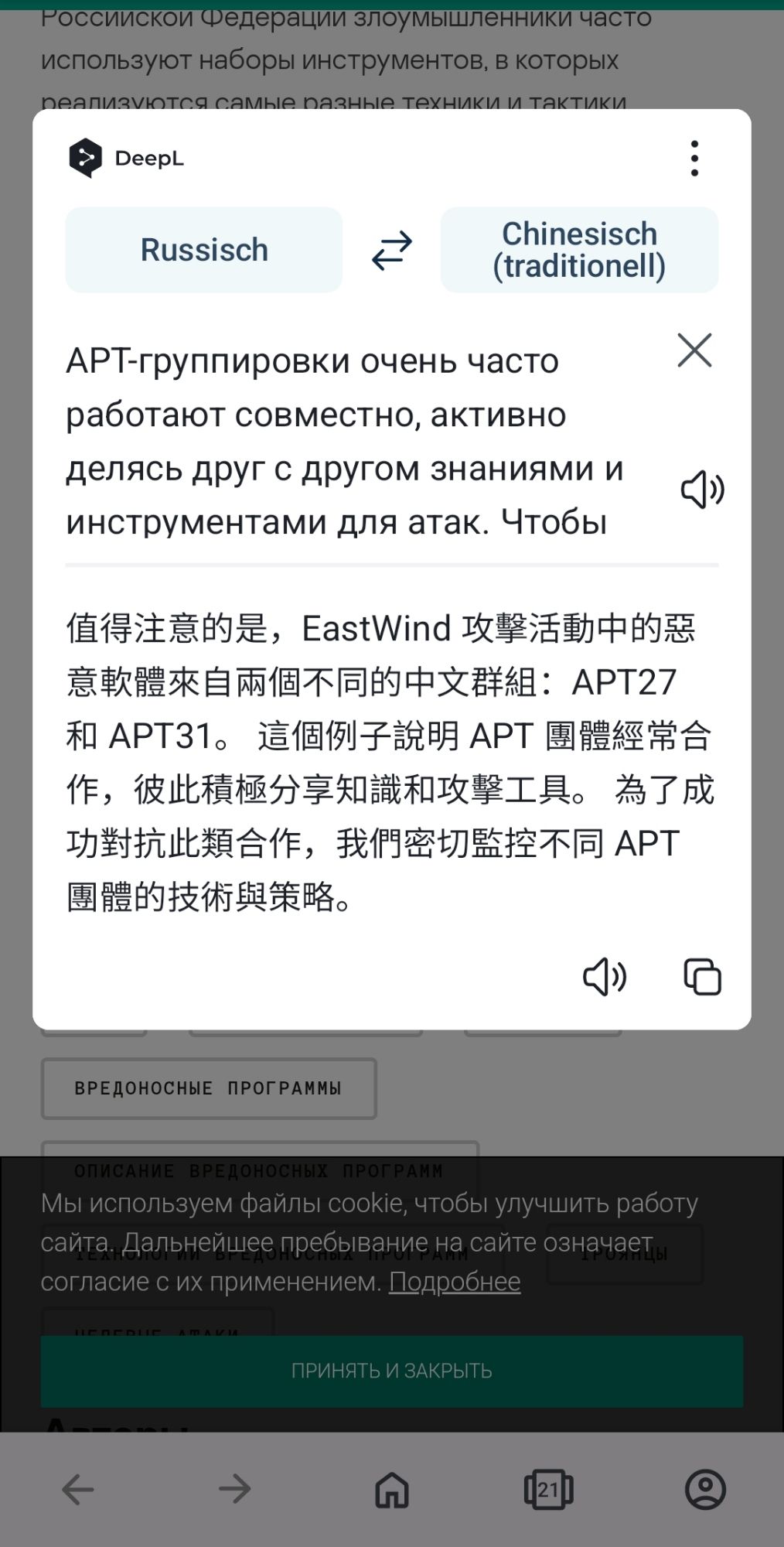
The Russia-based security biz claimed the malware used in the ongoing, targeted attacks – dubbed EastWind – has links to two China-nexus groups tracked as APT27 and APT31. www.theregister.com/2024/08/15/s...

No, no, go ahead, don't let us stop you, Xi
'EastWind' Potato-Spy Campaign Combines Various Chinese APT Tools
'EastWind' Cyber-Spy Campaign Combines Various Chinese APT Tools

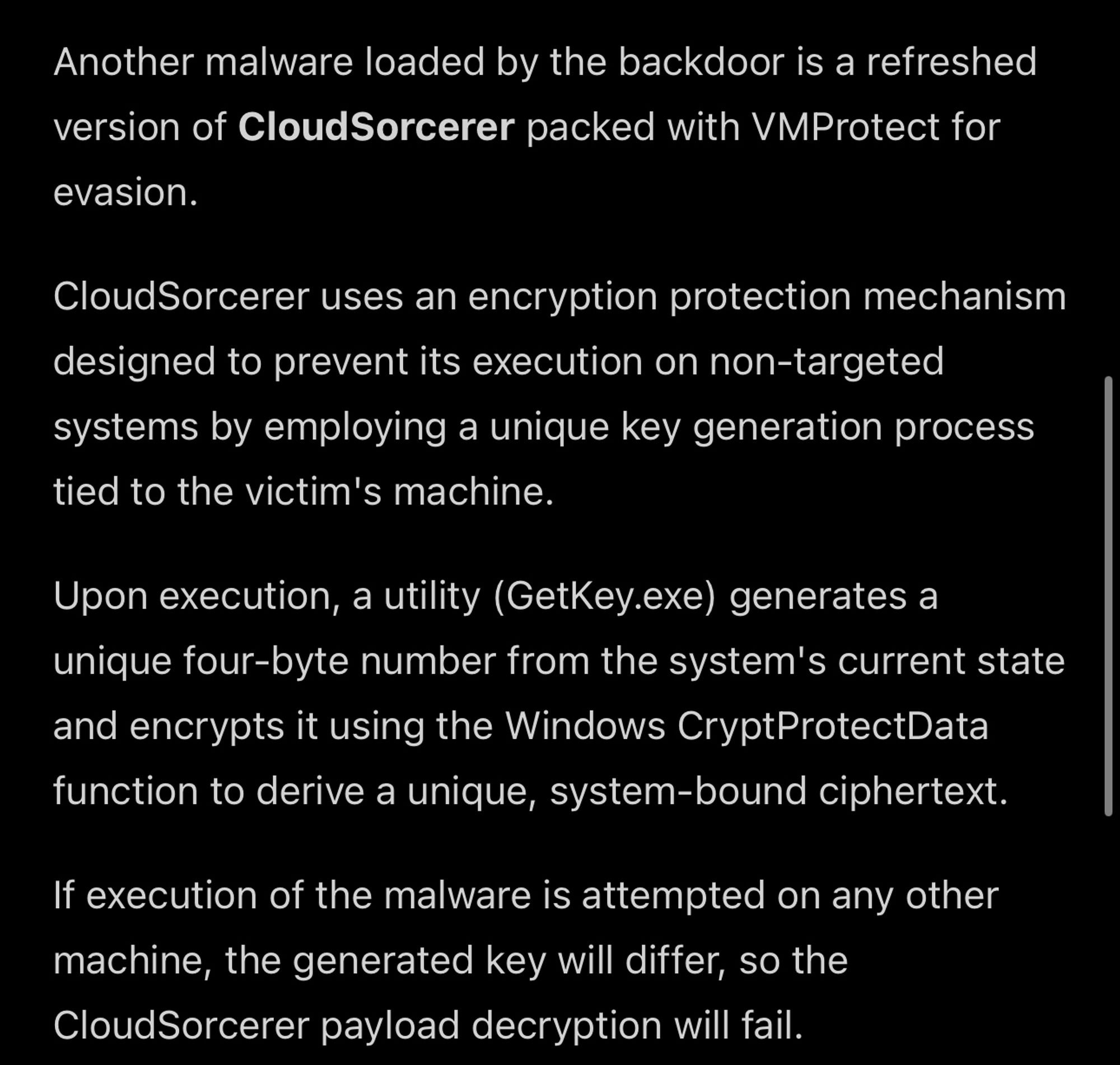
The likely China-linked campaign is deploying CloudSorcerer and other proprietary binaries belonging to known state-sponsored groups, showing how advanced persistent threat groups often collaborate with each other.
1/2 China launched a series of cyberattacks on Russian government organizations and IT companies. Some of the attack methods were previously unknown (meaning new). Is this what a “friendship without limits” looks like? With friends like these, who needs enemies?
Russian organizations face a new spear-phishing threat, EastWind, using PlugY #malwarethehackernews.com/2024/08/russ...#cybersecurity

Russian government and IT firms targeted by EastWind cyber campaign, deploying sophisticated malware through spear-phishing and watering hole attacks.