Related-Key Cryptanalysis of FUTURE (Amit Jana, Smita Das, Ayantika Chatterjee, Debdeep Mukhopadhyay) ia.cr/2024/1614

... en français (et en vrai ça pourrait être utile d'avoir chiffrer pour l'un et crypter pour l'autre) ; en anglais on distingue parfois encrypt et encipher pour ça je crois Dans ce cas la différence est vraiment importante car un chiffre par bloc offre zéro sécurité IND-CPA [...]
Останні пару днів я взагалі займався не грою, але devops штуками, як завжди. Маю тепер задеплоєний сервер на GCP Compute Engine, а ще мій ігровий сервер вміє в само-провізію TLS сертифікатів через Let's Encrypt (і піднімає тимчасовий порт для проходження HTTP-01 ACME челенджа)
bruh this whole time i thought signalis was just when u encrypt ur dick real good
It has been 17 days since I posted this, the mod is actually pretty much done now, I just need to figure it out a way to encrypt the files with no issues so I can finally post it on Nexus
Então, eu fiz assim a primeira versão, essa da PR o encrypt e decrypt acontece no navegador, o dado plain text nunca passa pelo servidor, ai o server guarda a privateKey pra o client descriptografar qnd o link for acessado.
We encrypt peoples books and movies so they have to spend extra electricity just to decrypt them when they want to watch them.
Fully Homomorphic Encryption for Cyclotomic Prime Moduli (Robin Geelen, Frederik Vercauteren) ia.cr/2024/1587
![Abstract. This paper presents a Generalized BFV (GBFV) fully homomorphic encryption scheme that encrypts plaintext spaces of the form ℤ[x]/(Φ_(m)(x),t(x)) with Φ_(m)(x) the m-th cyclotomic polynomial and t(x) an arbitrary polynomial. GBFV encompasses both BFV where t(x) = p is a constant, and the CLPX scheme (CT-RSA 2018) where m = 2^(k) and t(x) = x − b is a linear polynomial. The latter can encrypt a single huge integer modulo Φ_(m)(b), has much lower noise growth than BFV (linear in m instead of exponential), but cannot be bootstrapped.
We show that by a clever choice of m and higher degree polynomial t(x), our scheme combines the SIMD capabilities of BFV with the low noise growth of CLPX, whilst still being efficiently bootstrappable. Moreover, we present parameter families that natively accommodate packed plaintext spaces defined by a large cyclotomic prime, such as the Fermat prime Φ₂(2¹⁶) = 2¹⁶ + 1 and the Goldilocks prime Φ₆(2³²) = 2⁶⁴ − 2³² + 1. These primes are often used in homomorphic encryption applications and zero-knowledge proof systems.
Due to the lower noise growth, e.g. for the Goldilocks prime, GBFV can evaluate circuits whose multiplicative depth is more than 5 times larger than native BFV. As a result, we can evaluate either larger circuits or work with much smaller ring dimensions. In particular, we can natively bootstrap GBFV at 128-bit security for a large prime, already at ring dimension 2¹⁴, which was impossible before. We implemented the GBFV scheme on top of the SEAL library and achieve a latency of only 5 seconds to bootstrap a ciphertext encrypting 4096 elements modulo 2¹⁶ + 1.](https://cdn.bsky.app/img/feed_fullsize/plain/did:plc:fwa55bujvdrwlwlwgqmmxmuf/bafkreihdyifcgzlx7vn2lbg7myawfle5xsqaujmfoebeupzuoyubhpqqve@jpeg)

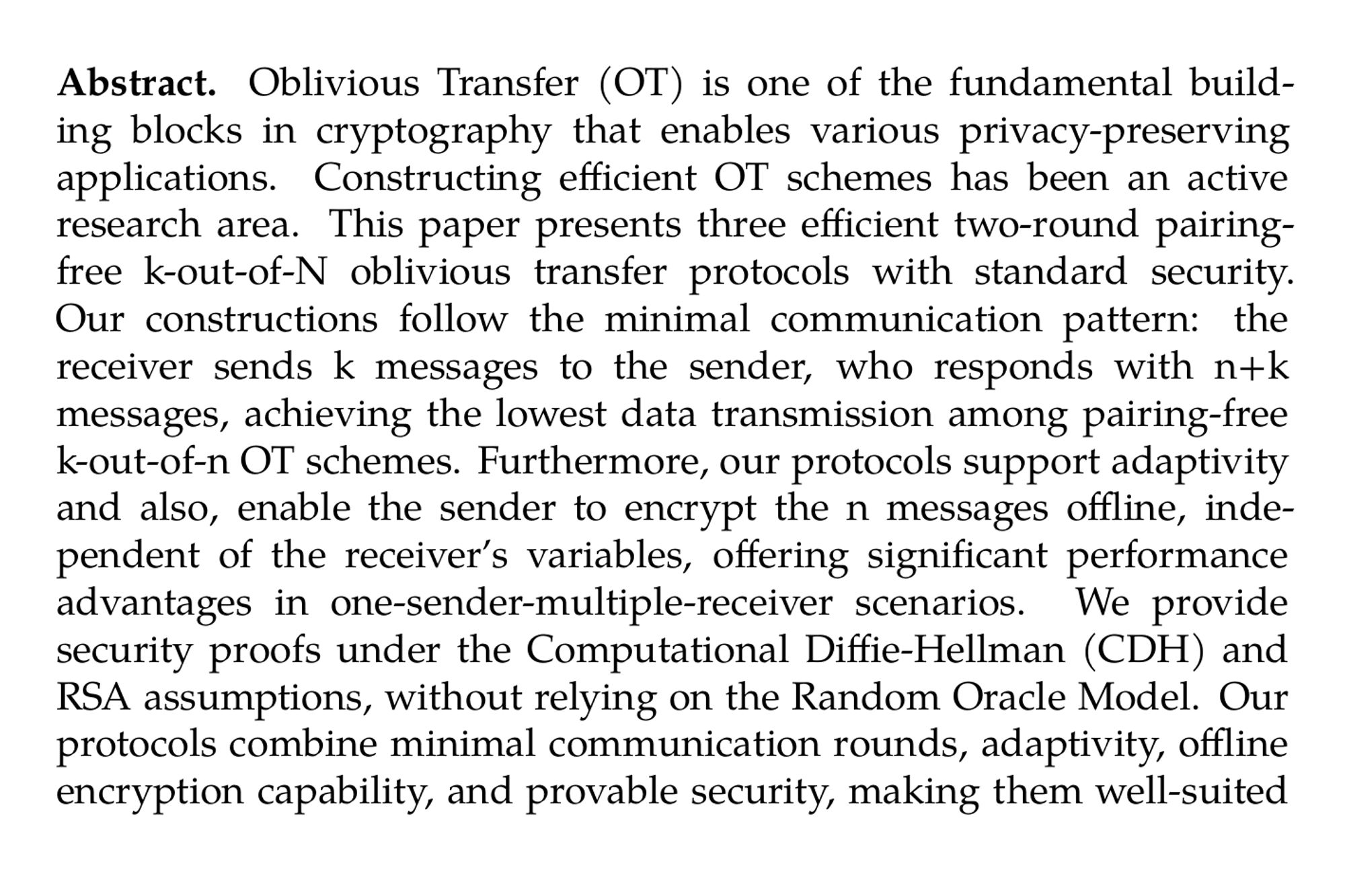
Efficient Pairing-Free Adaptable k-out-of-N Oblivious Transfer Protocols (Keykhosro Khosravani, Taraneh Eghlidos, Mohammad reza Aref) ia.cr/2024/1583