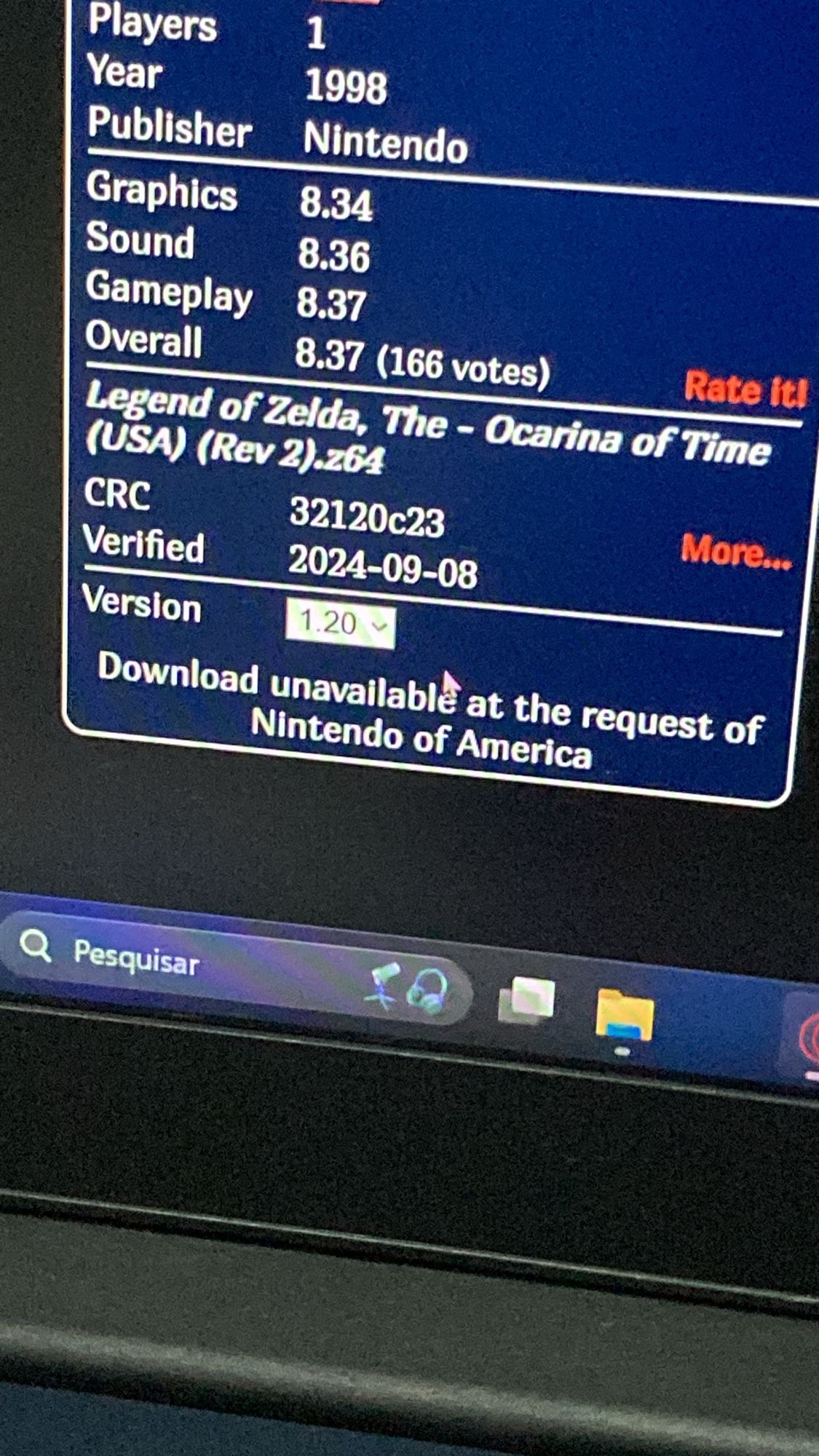
Gente alguem me manda um site bom pra baixar rom pfv quero jogar zelda💔💔💔
昨日のスペースROMってるときがめちゃくちゃ楽しかったので定期的にFFさんと対談してほしいですが……!?犬さんめちゃくちゃお話しするのお上手なのでまた待ってます…
Picard’s not sure what to make of the check-in protocol. Here’s to the first appearance of Vash! The Ferengi here is played by Max Grodénchik, who would later play Rom on DS9. #TNGSunNight#TOSSatNight

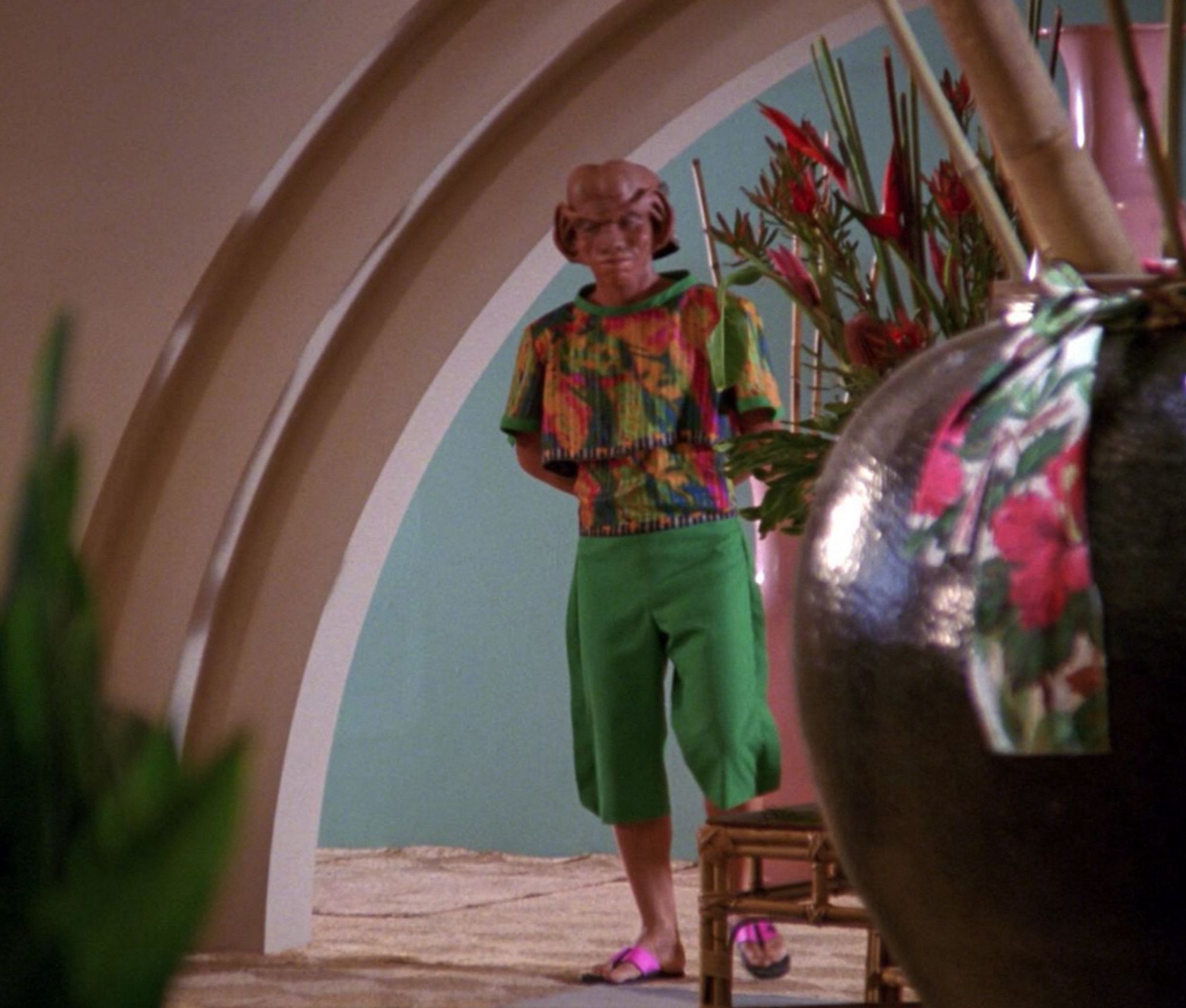

"to be penny-wise and pound-foolish“ beschreibt das Fehlverhalten, bei Pfennigbeträgen sparsam zu sein, aber gleichzeitig große Summen zum Fenster herauszuschmeißen, also „am falschen Ende zu sparen“ de.m.wikipedia.org/wiki/Pennywisede.m.wikipedia.org/wiki/Es_(Rom...

ah po, conheço o Light Platinum por sinal já tem uma cota que eu não pego pra jogar uma hack rom de GBA namoral as últimas q joguei foram as clássicas Pokémon Unbound e o grande Radical Red
Started Nobody Wants This on Netflix, rom/com with Kristin Bell and Adam Brody. Very funny and well written, fun back ‘n forth banter.
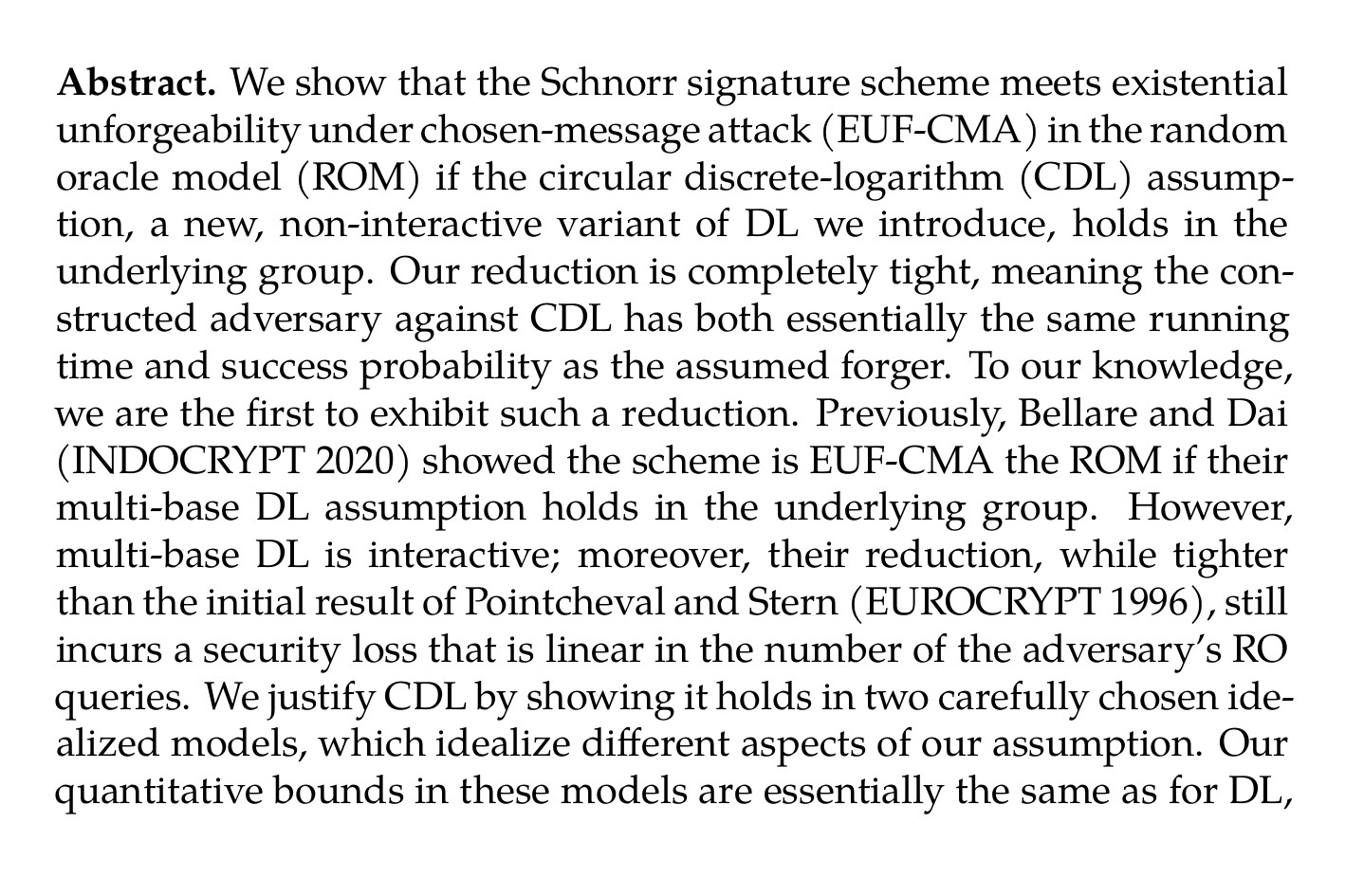
Schnorr Signatures are Tightly Secure in the ROM under a Non-interactive Assumption (Gavin Cho, Georg Fuchsbauer, Adam O'Neill) ia.cr/2024/1528

Pior que o unico Sonic bom que joguei era a hack rom do ligeirinho de NES onde ele salva o Mario.