Still can't believe we finally got kyber crystal bleeding in live action

ALT: a woman with dreadlocks is holding a light saber with the word kepler on the bottom right
Modelings for generic PoK and Applications: Shorter SD and PKP based Signatures (Slim Bettaieb, Loïc Bidoux, Philippe Gaborit, Mukul Kulkarni) ia.cr/2024/1668
kyber hi hi!!
Howdy Kyber :D
"Tu gosta de Star Wars? Então me explica como funciona o processo de fabricação do sabre de luz e todas as variantes do Cristal Kyber segundo a influência da Força." Galera tá acostumada a responder um ENEM quando podia tar beijando, vish.
CRYSTALS-Kyber(ML-KEM), CRYSTALS-Dilithium(ML-DSA), SLH-DSA(ML-DSA), FN-DSA 등 얄자내성암호 4개가 NIST 인증(FIPS)을 취득했습니다.
They state: "Our approach is motivated by the need to study more carefully the effect on security of using small secrets and small error in standardized LWE settings like Kyber and Homomorphic Encryption. In addition,They state: "Our approach is motivated by the need to study more carefully the effect on security of using small secrets and small error in standardized LWE settings like Kyber and Homomorphic Encryption. In addition,
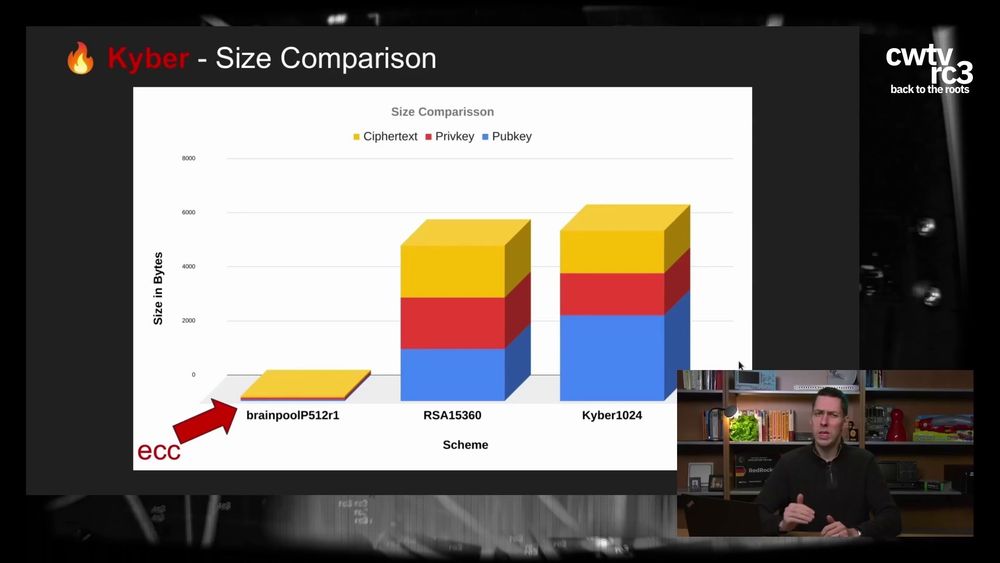
If someone is interested in how quantum resistant cryptography might work, there is this talk on Chrystals KYBER (FIPS 203 by NIST) that i can highly recommend.
Post-quantum crypto is being rolled out to secure **you** from quantum computers! Unfortunately, few people know how post-quantum works. ...
Bon je trouve aucune info sur Kyber qui tourne sur QUIC, a part les vidéos de conférence filmées. Je suis super curieux.