I guess, strategically and for the whole ecosystem, what would you see as the advantage of figuring out how to make OIDC work with atproto, if it required an "atproto profile of OIDC" that was different from regular OIDC?
the tailscale flow seems very similar to what we do with the atproto OAuth profile. it seems to me like the benefit of OIDC vs atproto OAuth profile is that adopters can use existing libraries. if they have to add a handle lookup box (like the tailscale email box) that won't work, right?
New release!!! @PersesDev v0.48.0 is hot off the presses, with some new visualizations for you: 📊 Metric finder 🥧 Pie chart panel 📜 Improved tracing display 🔐 OAuth & OIDC fully respecting OAuth 2.0 RFC ...a big shout out to all contributors! 📣 github.com/perses/perse...
This update introduces a brand-new Prometheus metric finder, based on the design from Prometheus 3.0 / Promlens, as well as a new Pie chart panel. Besides, It comes with multiple enhancements for t...
もちろん、Eventbriteではやりづらかったメリットの訴求(例えばDiscordをOIDCプロバイダに使うことでIDとの直接的な紐づけをするとか)もできるので、そこも書き出して比較する必要がある気はする。
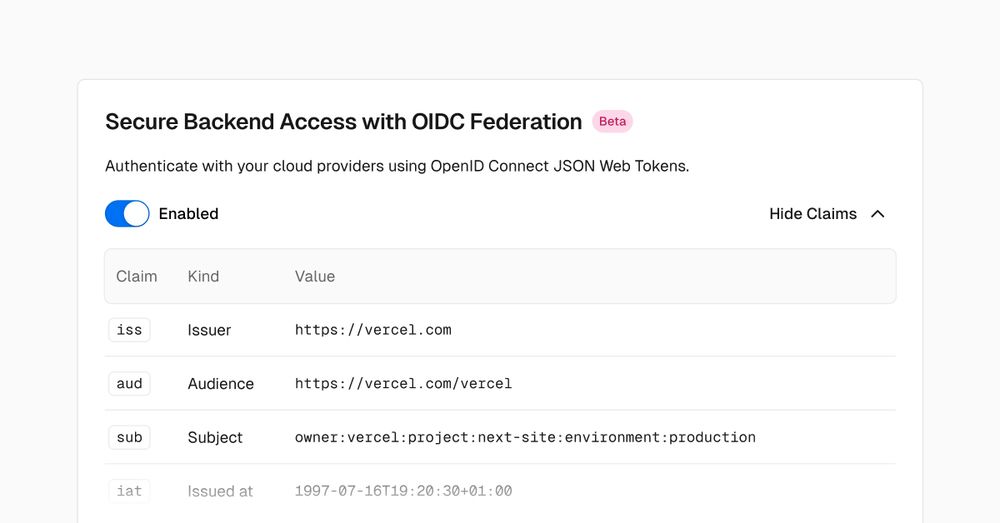
OpenID Connect (OIDC) Federation now available in Beta | Vercel News
The best way to deploy your Next.js site.
I would ask you to not give up on OIDC too easily. See for example the way Tailscale implements custom OIDC providers. You give them an email address, and they use WebFinger to look up the OIDC provider. I've found this to be an excellent way of doing things.
Since a "federated OAuth flavor with user IDs that can switch authority" (as is the case of did:plc), is inherently incompatible with OIDC (in which a client has to know, and trust, the authorities in advance), we didn't want to tie our specification with OIDC to avoid misleading devs.
We could borrow some OIDC stuff, such as the "/userinfo" endpoint. We didn't because we already have atproto endpoint to achieve this, and because we want to keep the requirements needed to implement a PDS as light as possibe.
At first, we tried to make our implementation OIDC compatible. As such "openid", "profile" scopes, id tokens and "/userinfo" were all supported. Then we realized that there is a fundamental incompatibility between OpenID and our user identifiers. So we dropped most of the OIDC code.
The main issue isn't that it returns extra data, it's that `sub` is a DID, and you need to resolve that DID before you can trust that AS as authoritative for it. The protocol also requires use of the `atproto` scope. But I don't think either of these necessarily make it non-OIDC compatible.