Printed the text from a text-only Word/.docx file into markdown and org to compare file sizes just out of curiosity. The .docx was almost 10x as large as the .md file. #plaintext
that's a security thing chromium tries saving secrets via secret service rather than in plaintext, and kde's secret service implementation happens to be kwallet but honestly you should probably use gnome-keyring, kwallet's crypto is sketchy as best
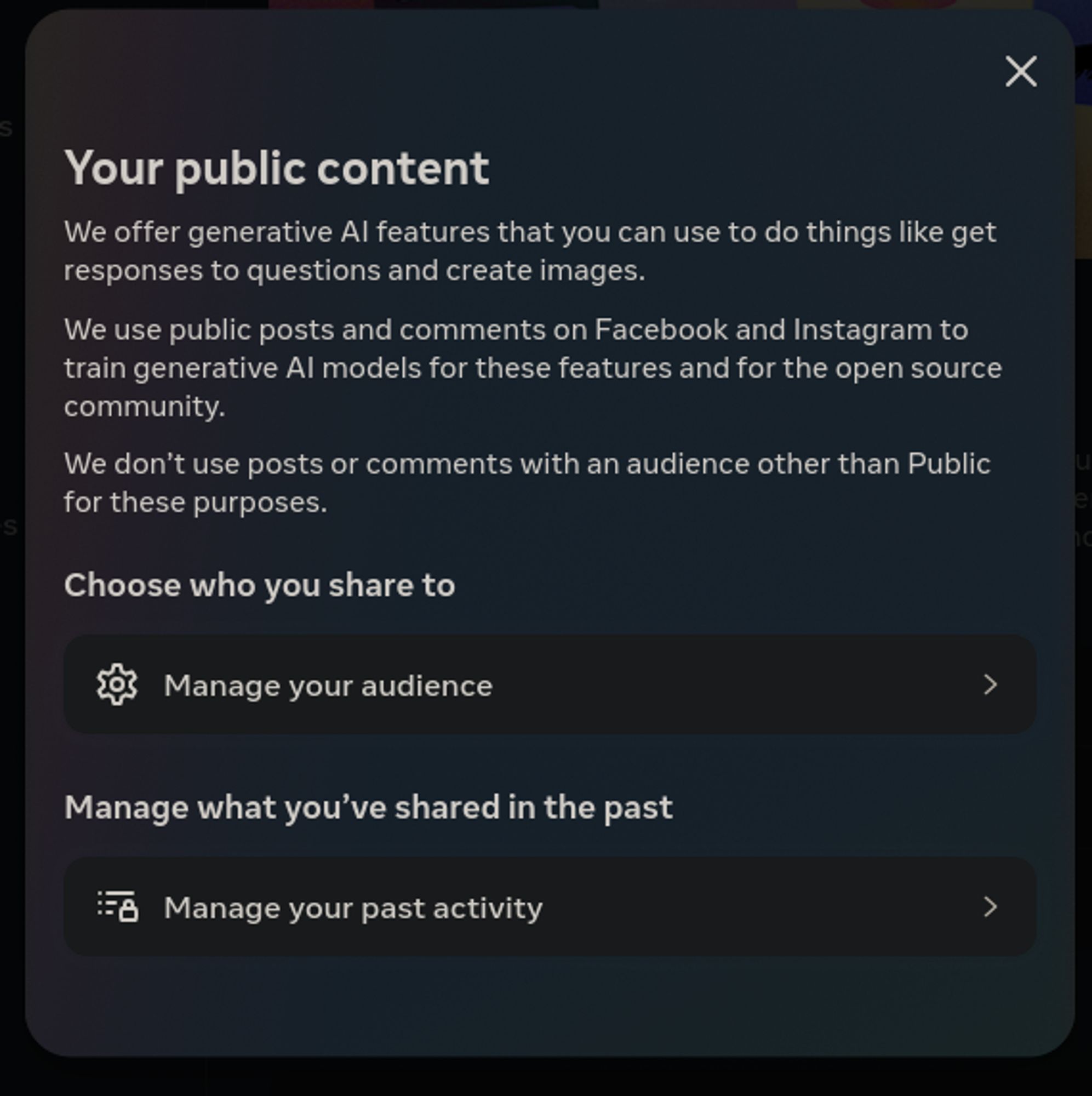
While trying to properly document Meta's use of public content for LLM training, I discovered they have a new "Privacy Center" that is _not_ plaintext by any means. Direct link: privacycenter.instag...
Intent to prototype: contenteditable=plaintext-only groups.google.com/a/mozilla.or...
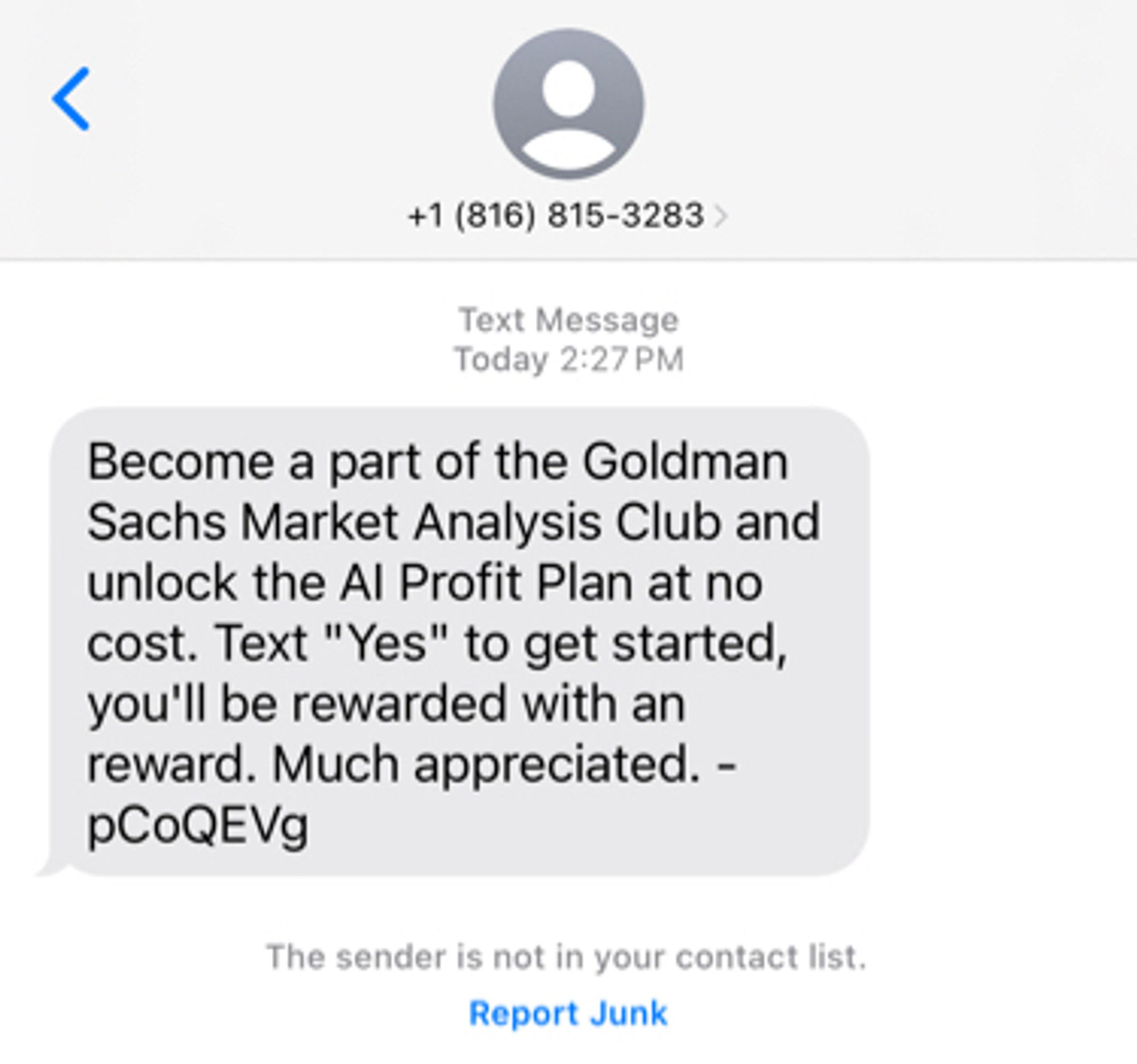
Why, yes I will respond to a random number from Kansas City using perfect English grammar to offer getting me started in the Goldman Sachs AI Profit Plan. This is obviously credible and I will give them my social security number in plaintext.
por que os ANIMAIS do congresso brasileiro de neurologia gravaram minha senha como plaintext e me mandaram SEM EU PEDIR em um e-mail?
Meta fined $101 million for storing hundreds of millions of passwords in plaintext #potatosecurity#infosec#privacy#news therecord.media/meta...
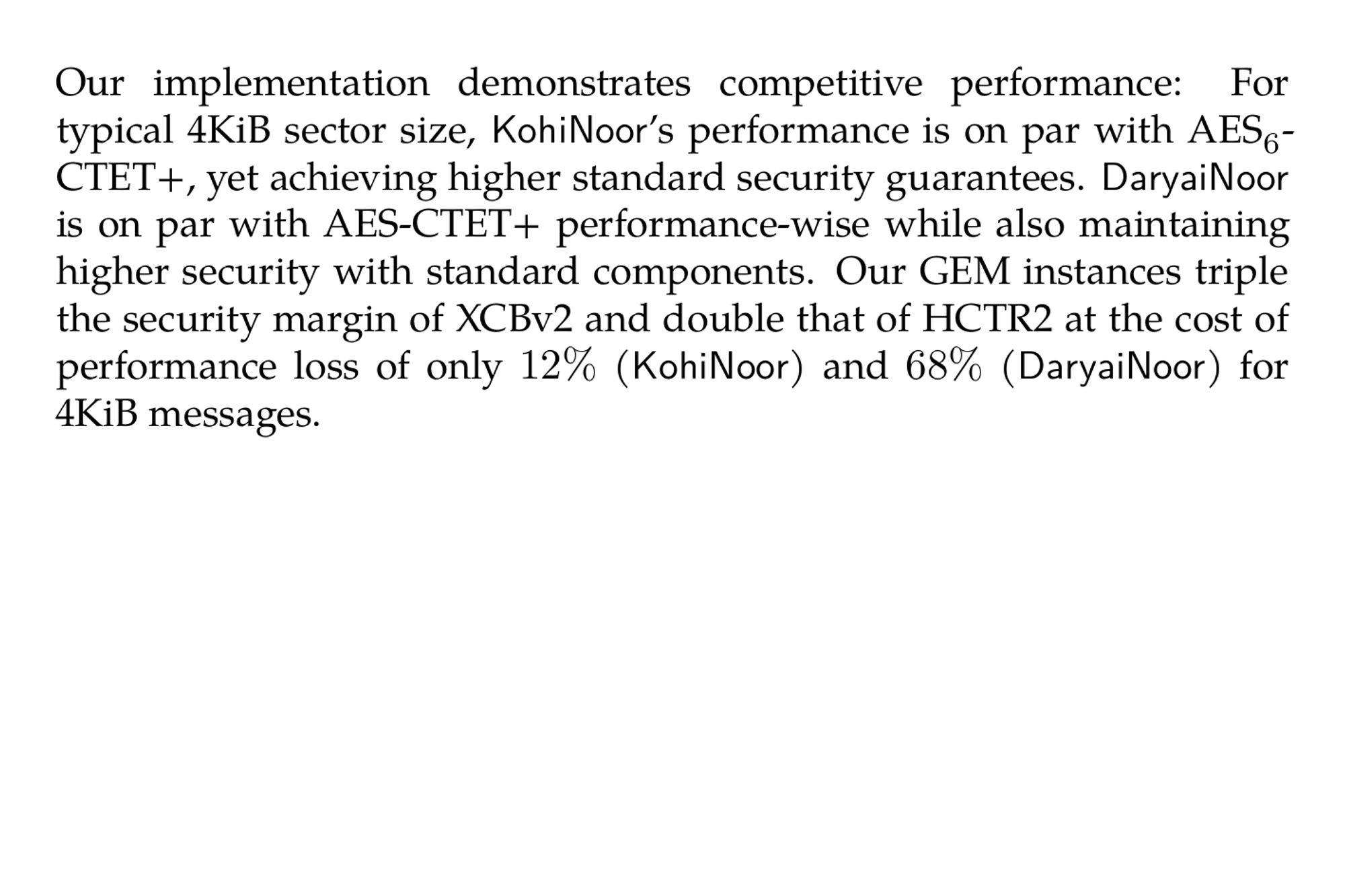
Breaking, Repairing and Enhancing XCBv2 into the Tweakable Enciphering Mode GEM (Amit Singh Bhati, Michiel Verbauwhede, Elena Andreeva) ia.cr/2024/1554


More Efficient Lattice-based OLE from Circuit-private Linear HE with Polynomial Overhead (Leo de Castro, Duhyeong Kim, Miran Kim, Keewoo Lee, Seonhong Min, Yongsoo Song) ia.cr/2024/1534

Meta fined $101 million for storing hundreds of millions of passwords in plaintext #cybersecurity#infosec#privacy#newstherecord.media/meta...

European regulators fined Meta for an engineering mistake that the social media giant first reported in 2019.