EU
ePrint Updates
@eprint.bsky.social
Unofficial bot tracking updates to the IACR Cryptology ePrint Archive (eprint.iacr.org/). Maintained by @str4d.xyz.
Currently only posts about new papers. Author names are linkified to Bluesky accounts; contact maintainer for inclusion or removal.
405 followers1 following2.8k posts
On Sequential Functions and Fine-Grained Cryptography (Jiaxin Guan, Hart Montgomery) ia.cr/2024/1050
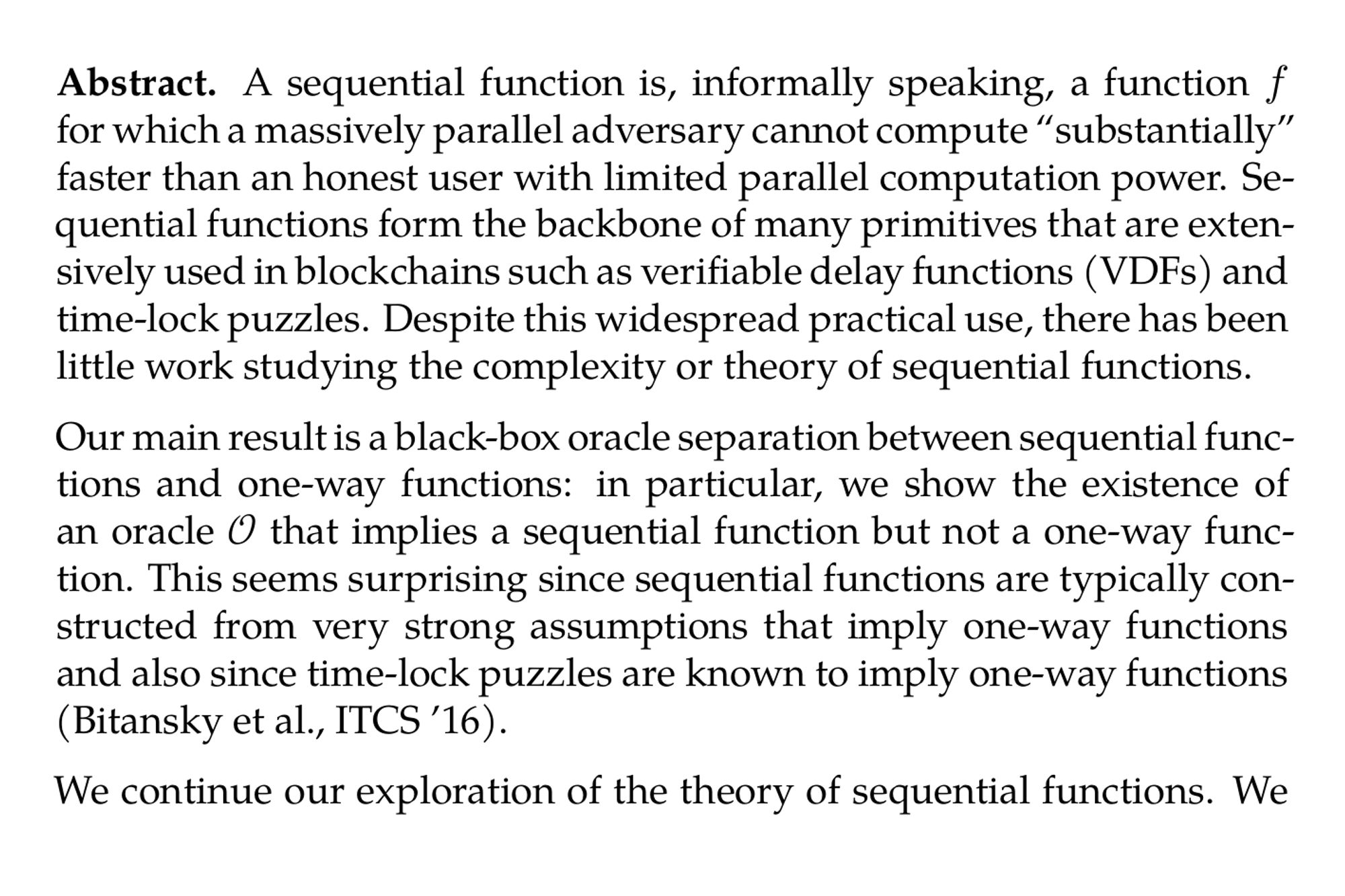


EU
ePrint Updates
@eprint.bsky.social
Unofficial bot tracking updates to the IACR Cryptology ePrint Archive (eprint.iacr.org/). Maintained by @str4d.xyz.
Currently only posts about new papers. Author names are linkified to Bluesky accounts; contact maintainer for inclusion or removal.
405 followers1 following2.8k posts