My department is recruiting two lecturers (~ assistant professors) www.kcl.ac.uk/jobs/096025-... Cryptography is not high on the list of priorities for these ones, though.

We are happy to announce the release of OpenMLS v0.6, a significant update to our open-source MLS implementation. This version includes several new features and improvements. Read all details on the blog: https://buff.ly/47aL5dz#MLS#opensource#cryptography
We are hiring a postdoc at LMU's Munich Center for Mathematical Philosophy. Areas: decision theory, social choice theory, philosophy of action, the study of agency & free will, and/or related themes in the philosophy of mind. Deadline 8 Sept. Please spread the word. job-portal.lmu.de/jobposting/4...
At @SandboxAQ we're hiring for an engineering consulting position in the areas of (post-quantum) cryptography or privacy: www.iacr.org/jobs/item/3716 part-time or full-time.
Postdoc Position in Cryptography: Social Foundations of Cryptography: martinralbrecht.wordpress.com/2024/06/11/c...social-foundations-of-cryptography.gitlab.io

We are looking for a postdoc to work with us on the social foundations of cryptography. This is a two-year full-time position based in London at a salary of £47,978 per annum. We. This postdoc positio...
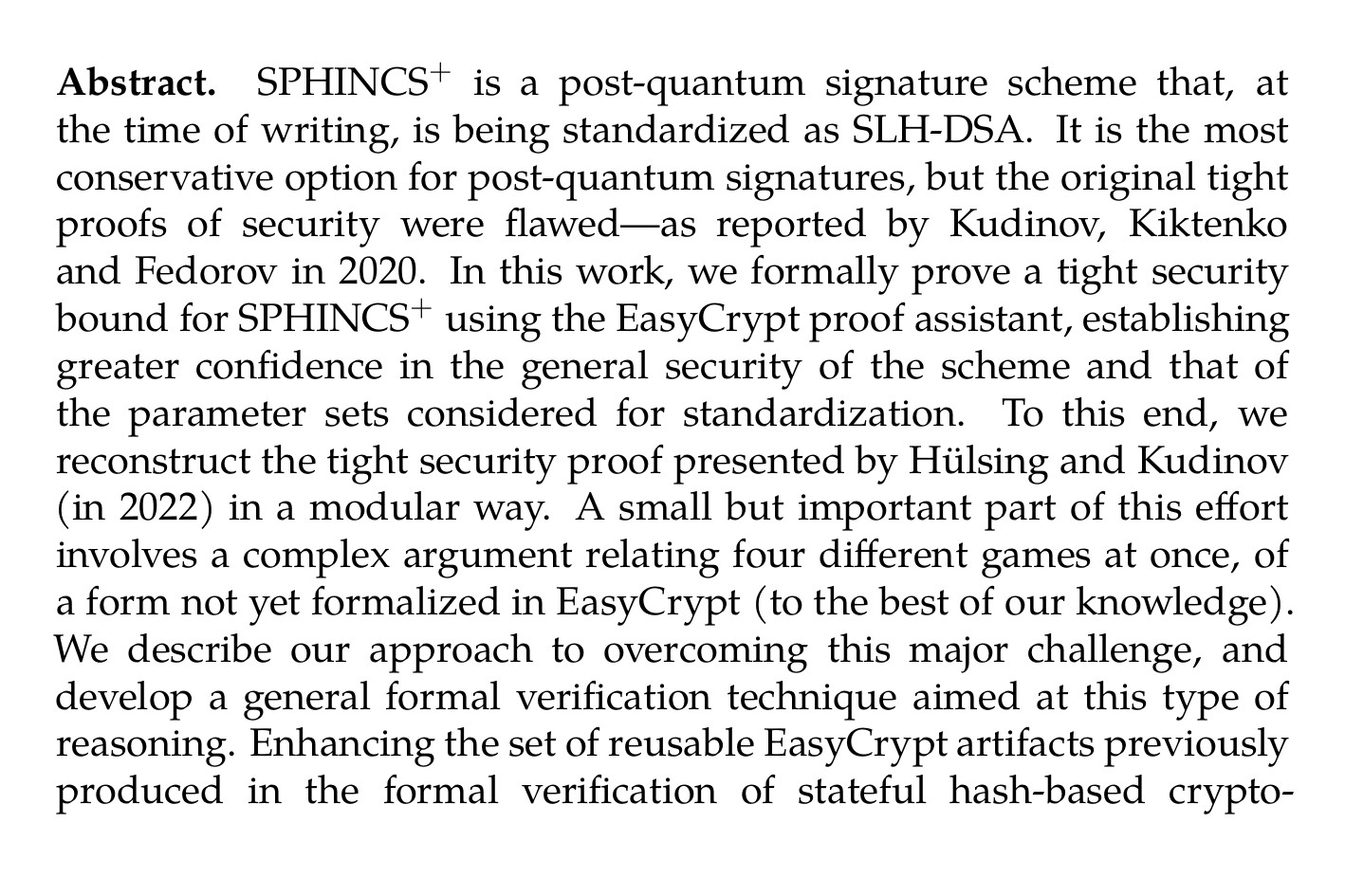
A Tight Security Proof for SPHINCS⁺, Formally Verified (Manuel Barbosa, François Dupressoiria.cr/2024/910

The University of Bristol is looking to grow its verification activities. A lectureship in verification is open in an adjacent group. The group itself is very project-driven, with the environment around it giving a nice mix of curiosity- and mission-driven groups. www.bristol.ac.uk/jobs/find/de...
We are looking for a postdoc to work with us on lattice-based cryptography: www.kcl.ac.uk/jobs/090126-...malb.io/sis-with-hin...martinralbrecht.wordpress.com/2023/01/31/e...

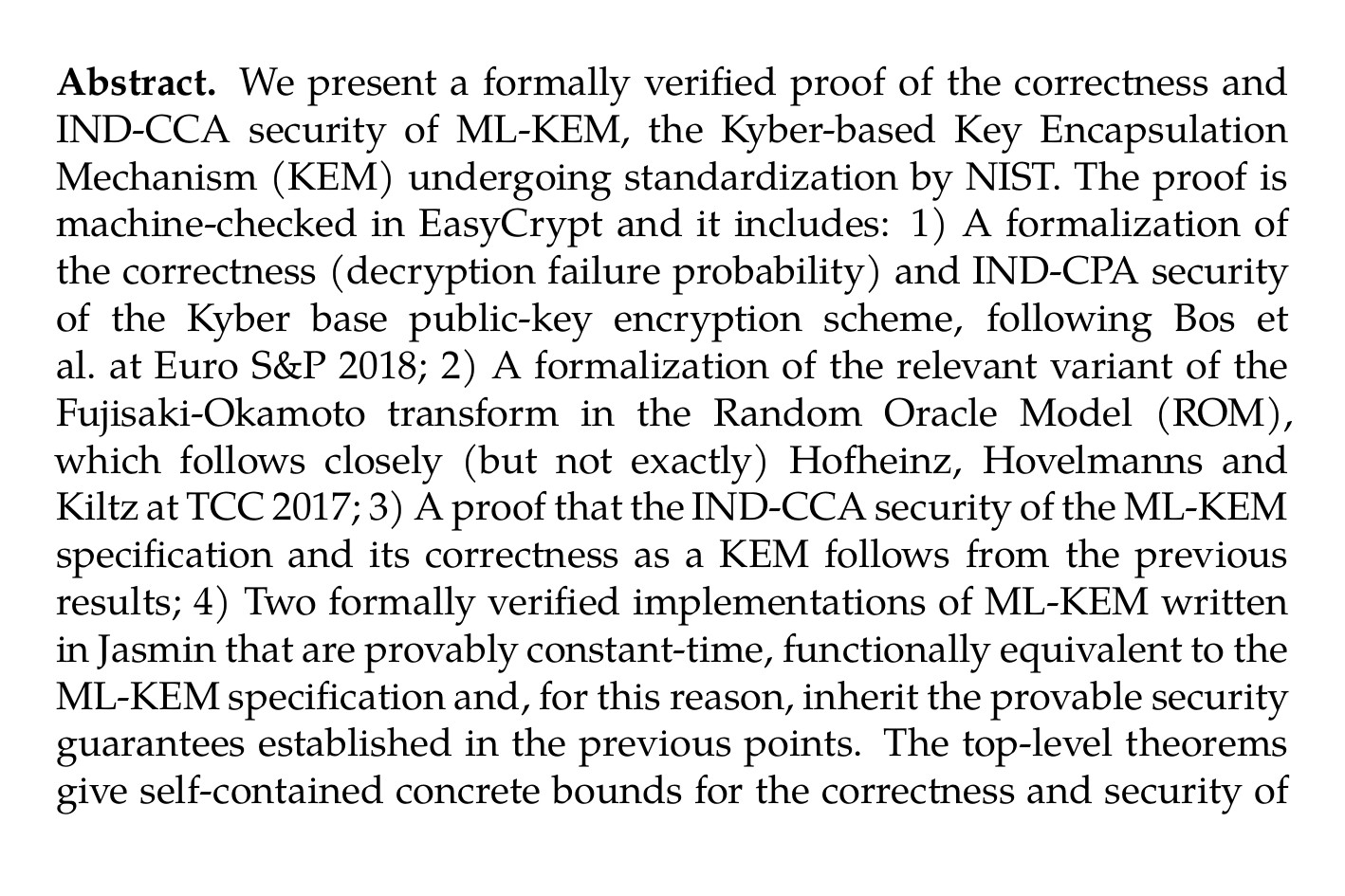
Formally verifying Kyber Episode V: Machine-checked IND-CCA security and correctness of ML-KEM in EasyCrypt (José Bacelar Almeida et al.ia.cr/2024/843