
But how can it be quantum and still only 'Pretty Good'?
We are hiring a postdoc at LMU's Munich Center for Mathematical Philosophy. Areas: decision theory, social choice theory, philosophy of action, the study of agency & free will, and/or related themes in the philosophy of mind. Deadline 8 Sept. Please spread the word. job-portal.lmu.de/jobposting/4...
You really shouldn't give Edam. Raclette them talk.
Maybe I'll add a note that I am not Satoshi to my website as well.
At @SandboxAQ we're hiring for an engineering consulting position in the areas of (post-quantum) cryptography or privacy: www.iacr.org/jobs/item/3716 part-time or full-time.
> Benjamin Dowling, who is a cryptographer at Sheffield University (soon King’s College London) (Proper and official) Congratulations to both of youse.
Postdoc Position in Cryptography: Social Foundations of Cryptography: martinralbrecht.wordpress.com/2024/06/11/c...social-foundations-of-cryptography.gitlab.io

We are looking for a postdoc to work with us on the social foundations of cryptography. This is a two-year full-time position based in London at a salary of £47,978 per annum. We. This postdoc positio...
Rogue mass-transferred with Ruby because the trap was full (set to a capacity of 6) when he stepped into it. It wasn't yet full when he threw Emily into it.
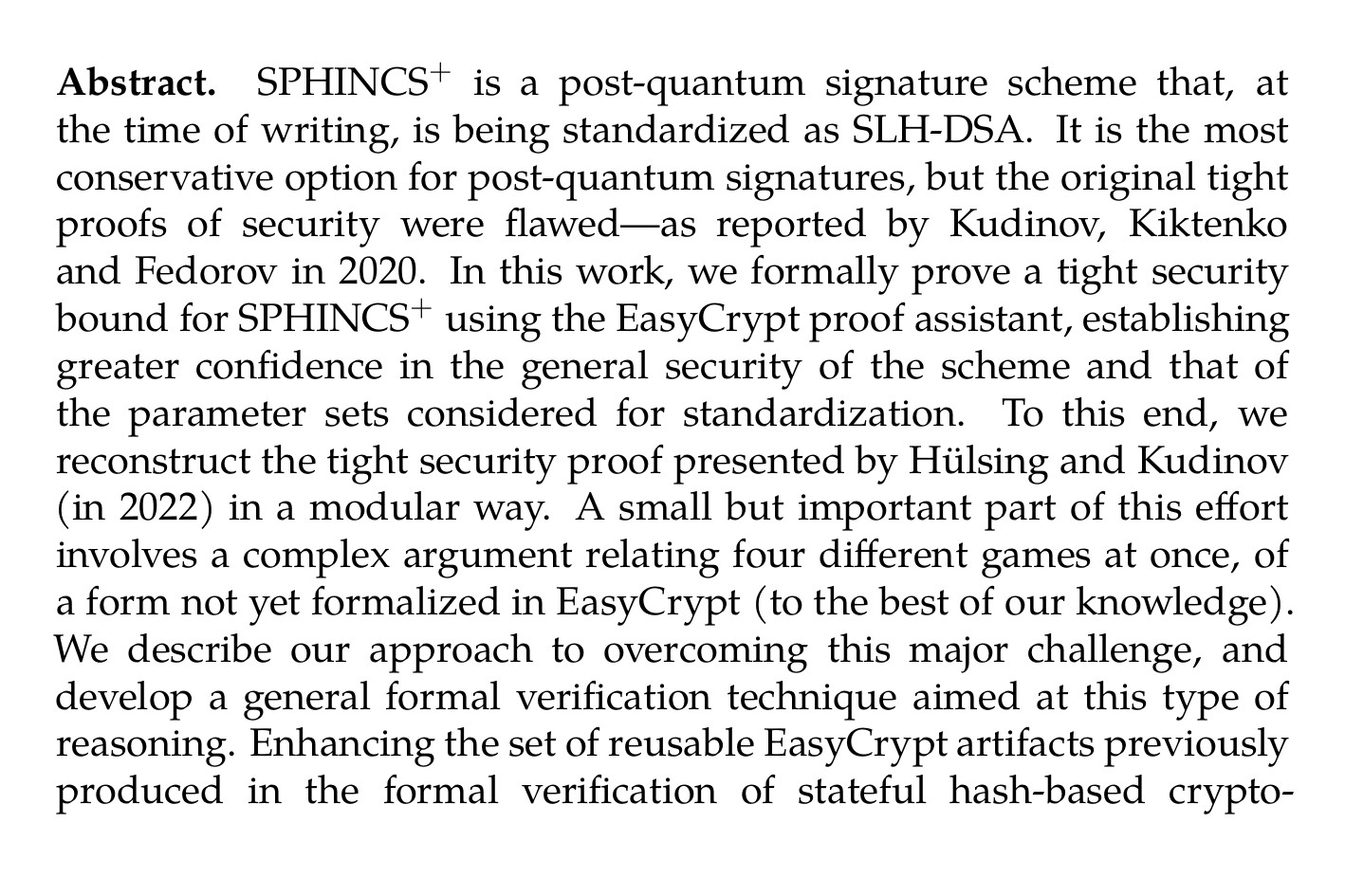
A Tight Security Proof for SPHINCS⁺, Formally Verified (Manuel Barbosa, François Dupressoiria.cr/2024/910

Compilation. Not even once.
