The best part of Counterpoint is that Sivaraman's approach easily enables a low-level accessibility toolkit like Data Navigator by converting state into a graph structure. This makes Counterpoint one of the first projects of its kind!! See the demo: dig.cmu.edu/counterpoint...
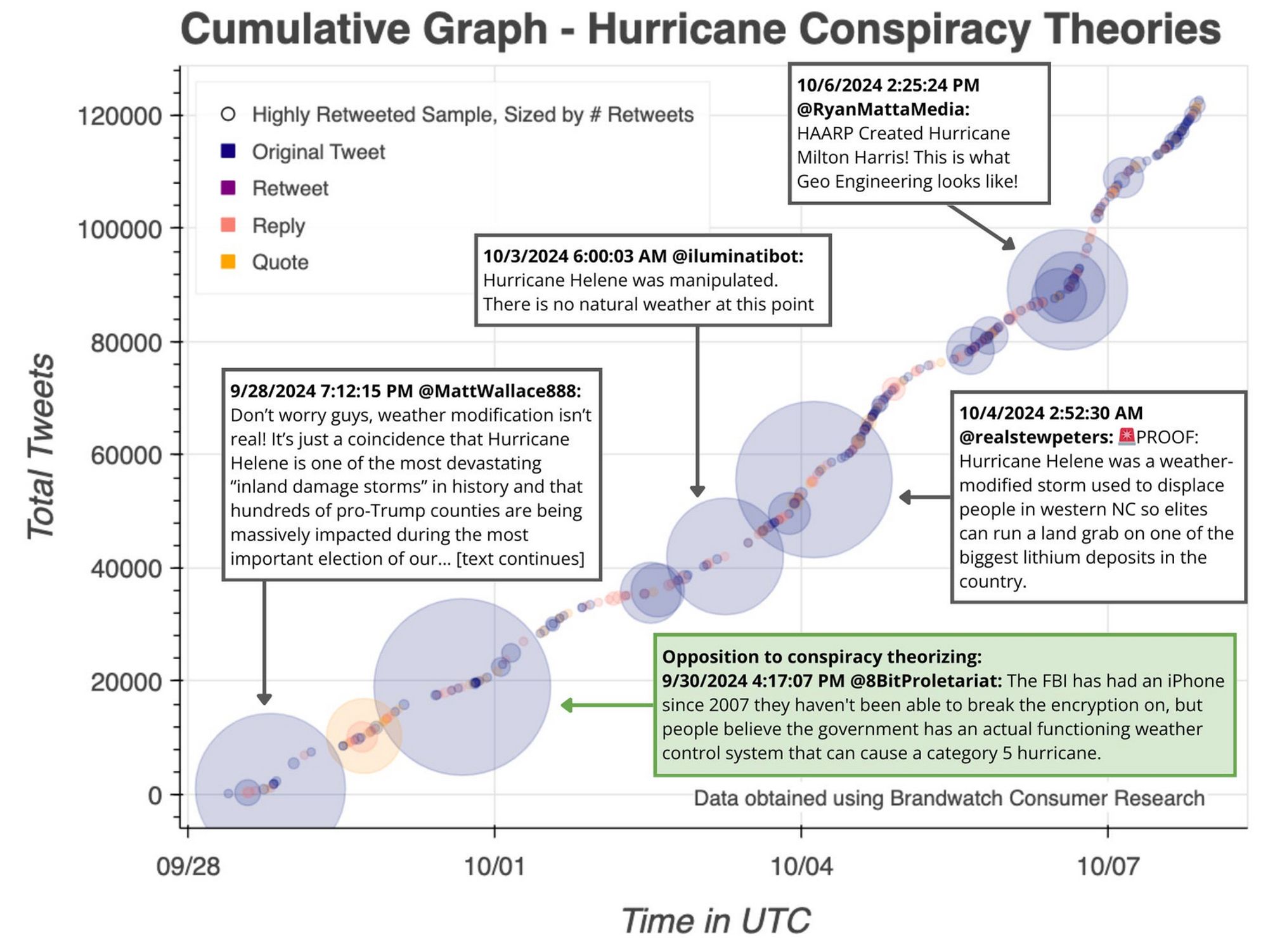
The wildest rumors, which many of you have heard about, are conspiracy theories that Democrats control the weather and intentionally created the hurricane to impact voting in red states. We tracked how those rumors spread on X, mapping highly-retweeted tweets along a cumulative graph:
BTW, this all probably sounds obvious. But I used to find it helpful in risk assessments when someone would create a crazy narrative to justify the impact of a risk. Often times the narrative could be abstracted away to one of the 3 w/ the problem being narrative supplied physical or root access.
The practice went out of favor as gardens became more a showplace for exotic and showy plants and flowers, less a reflection of an idealistic vision of nature pre-civilization. You can read more here:

Wealthy landowners hired men who agreed to live in isolation on their estates for as long as seven years
Gabe's 3 rules of security: 1. Anyone with physical access to a computer can deny availability. 2. Anyone with root can do anything. 3. Anyone with unfettered physical access can become root. caveat: immutable logs
In the broad strokes, I generally disagree with it and put it in roughly the same bin as an over-reliance on radicalization narratives, but I DO think a nonzero amount of the vague, incoherent, and atavistic urge towards a libertarianism to "recover" society fits in with that model.
A thought I always have on the way to things like this some of their support is the one thing that makes me sympathetic to the "confused conspiracist" narrative—the idea a lot of these people correctly assess there's something wrong in our society but fail to draw coherent conclusions about what.
If it's reactive with moisture And it's just sitting out I have other questions. Since, you know, humidity.
A great philosopher recently told me: "you can always get away with saying 'I think you'll find it's more complicated than that', because it's always true. But it's not always helpful."
