
K
ky.le
@polyrhyth.ms
bird nerd, art fiend, internet enthusiast
music blog: polyrhyth.ms
photo portfolio: indiffe.rent
rave music radio: radio.ravemix.es
discord: seltzeraddict
he/him | ?
476 followers294 following3.2k posts
Do we know if it was exploited in the wild at all before it was found?
if this was known, I imagine the patch would've been pushed out way faster
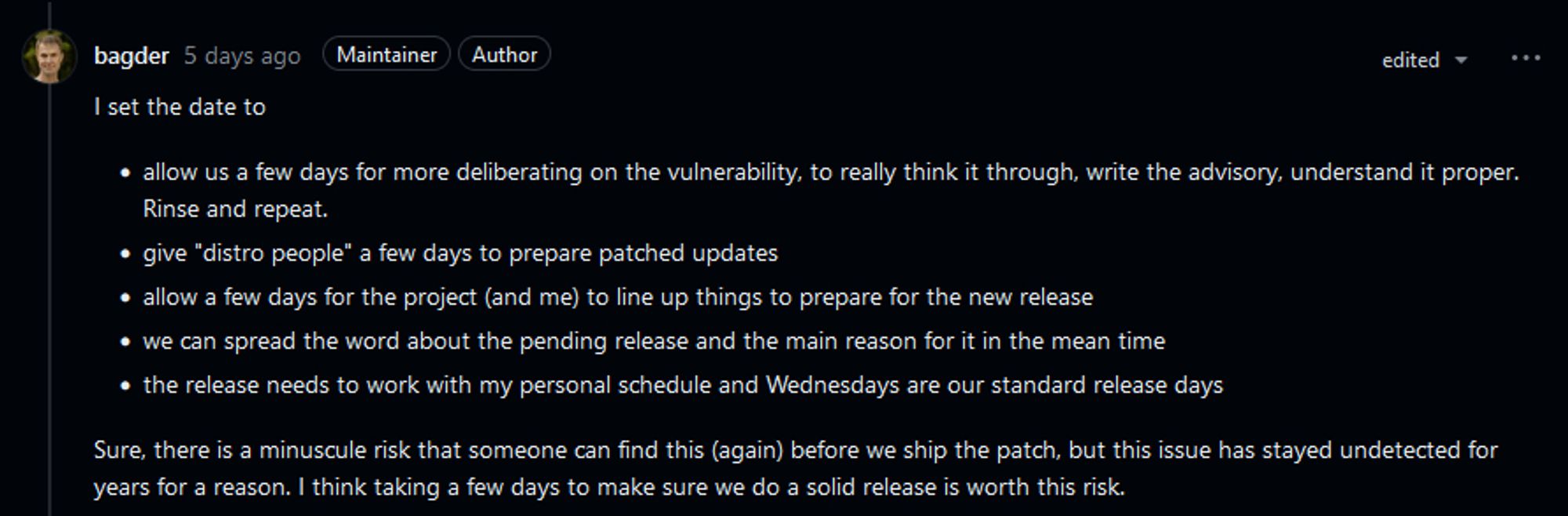
this is the main reply from a dev gives some context and hints that they are not seeing nor hearing about this exploited in the wild there doesn't appear to be a public exploit available either, but I'll admit I just did a cursory search

K
ky.le
@polyrhyth.ms
bird nerd, art fiend, internet enthusiast
music blog: polyrhyth.ms
photo portfolio: indiffe.rent
rave music radio: radio.ravemix.es
discord: seltzeraddict
he/him | ?
476 followers294 following3.2k posts