If you receive a report about a compromised device, please investigate immediately. Look for webshell file named "update.php" in the "/root/webviewer/" directory.
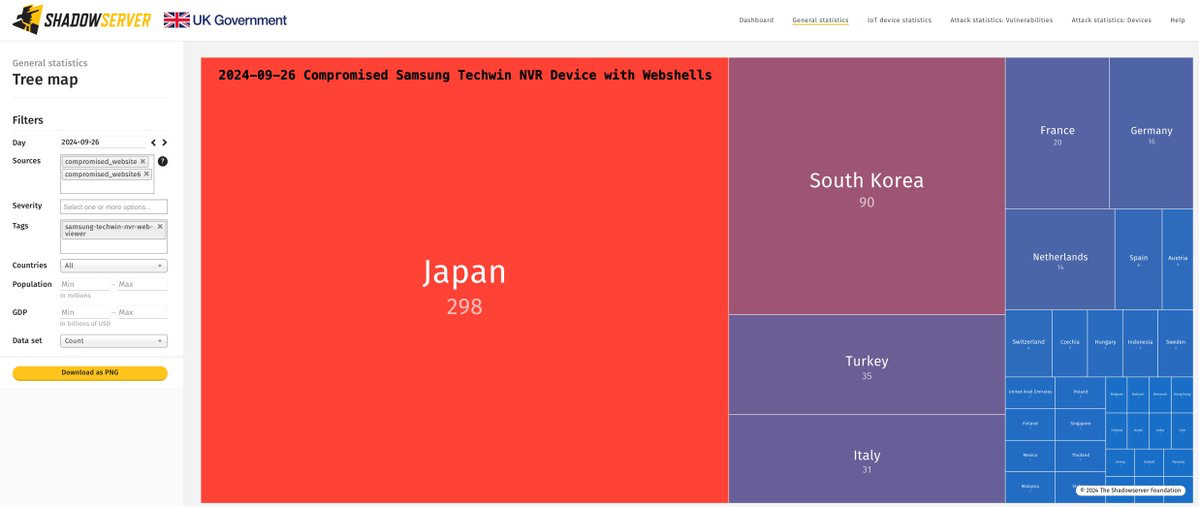
Statistics about compromised publicly exposed devices are available on our Dashboard (~600 devices initially). Treemap of devices per country: dashboard.shadowserver.org/statistics/c...dashboard.shadowserver.org/statistics/c...
Thanks to collaboration with the Saudi NCA we now detect Samsung Techwin NVR Web Viewer devices compromised with a webshell (backdoor). Data added to our free daily Compromised Website Report from 2024-09-26: shadowserver.org/what-we-do/n... Events tagged as "samsung-techwin-nvr-web-viewer"
Background on recent CUPS RCEs: www.evilsocket.net/2024/09/26/A...
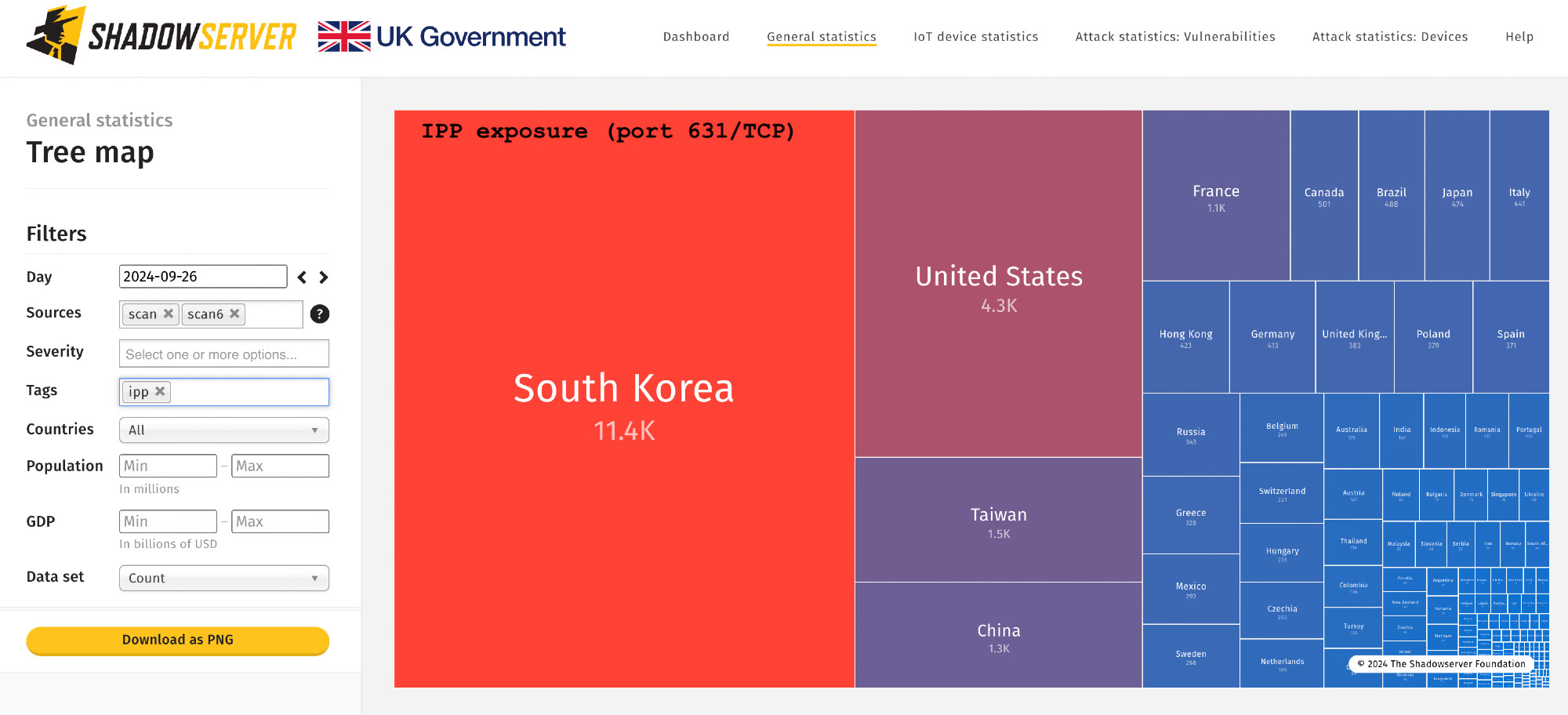
IP data on exposed printer instances on port 631/TCP in our Open IPP report: shadowserver.org/what-we-do/n...dashboard.shadowserver.org/statistics/c...
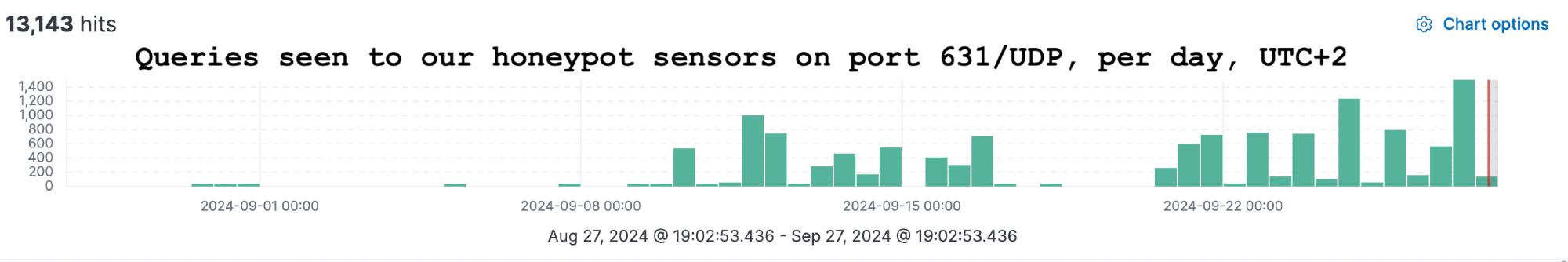
Large increase in queries on 631/UDP seen in our sensors due to recent CUPS RCEs disclosure. These include callback attempts. We are exploring possible non-invasive scanning options for the recent RCEs. Please note we scan daily for exposed IPP printer services (631/TCP).
Other AI/LLM/Chatbot platform CVE attempts we track include for example NextChat CVE-2023-49785, LiteLLM CVE-2024-6587, Ollama CVE-2024-37032, dirk1983/chatgpt CVE-2024-27564 Expect more to come ...
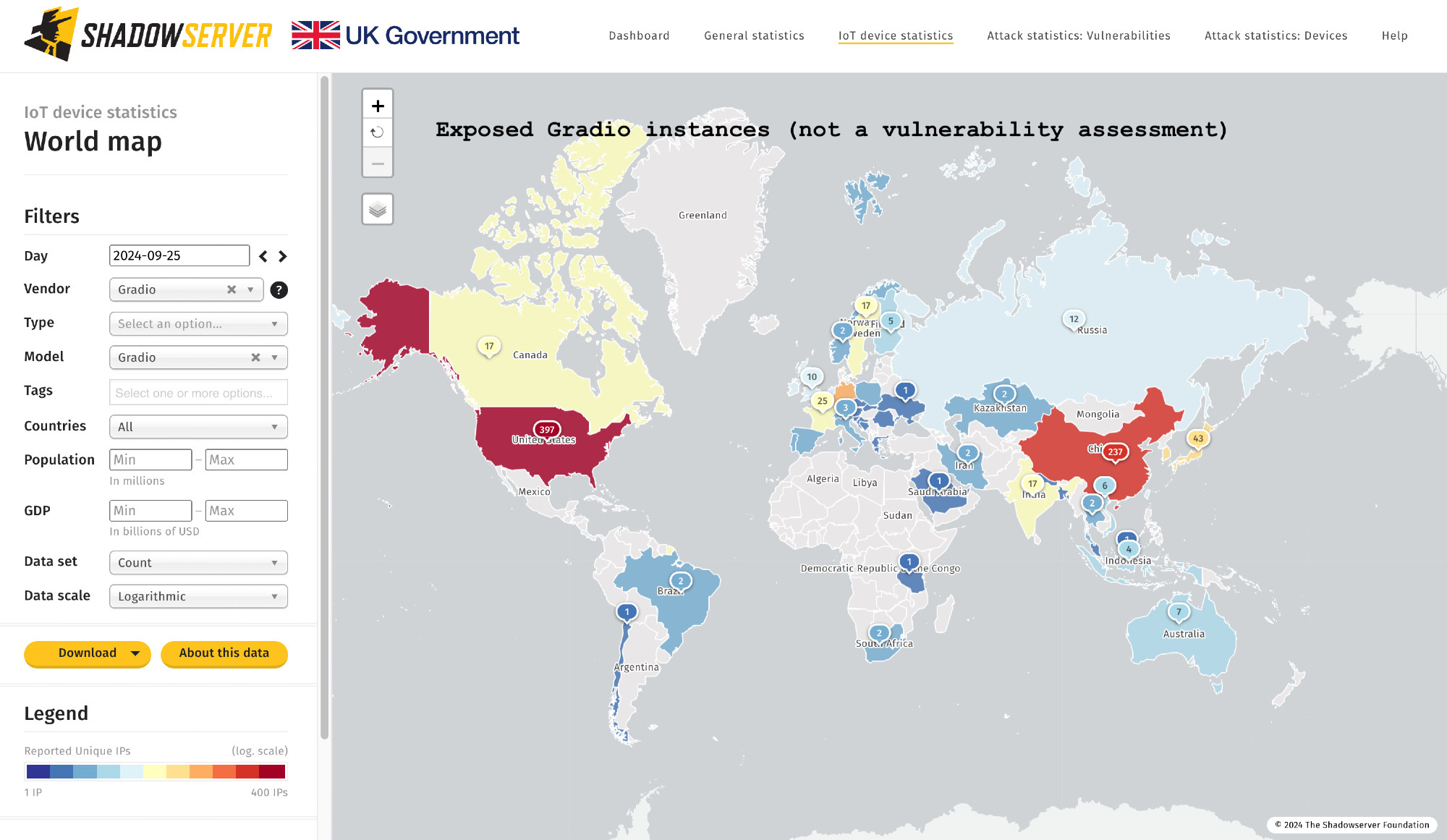
Gradio exposure (no vulnerability assessment): over 1000 IPs seen worldwide. Top: US (397), China (237), Germany (52). Shared in our Device ID report: shadowserver.org/what-we-do/n...dashboard.shadowserver.org/statistics/i...gradio.app/changelog
We are seeing an increase in attacks against various AI/LLM platforms. This includes Gradio CVE-2024-4325 SSRF (since end of June), CVE-2024-1561 path traversal (start of July). Tags for these are now visible on our Dashboard & tracked moving forward. dashboard.shadowserver.org/statistics/h...
This complements our other reports such as the Compromised Website report with HTTP based detection (see shadowserver.org/what-we-do/n...) which also contains IoT devices, as well as our sinkhole and honeypot based reports. The report will be expanded with new detections in the future.