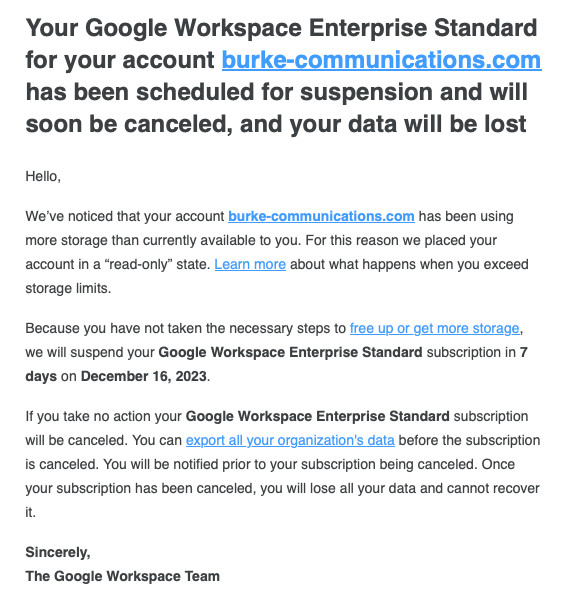
More reasons to avoid trusting Google with your data.
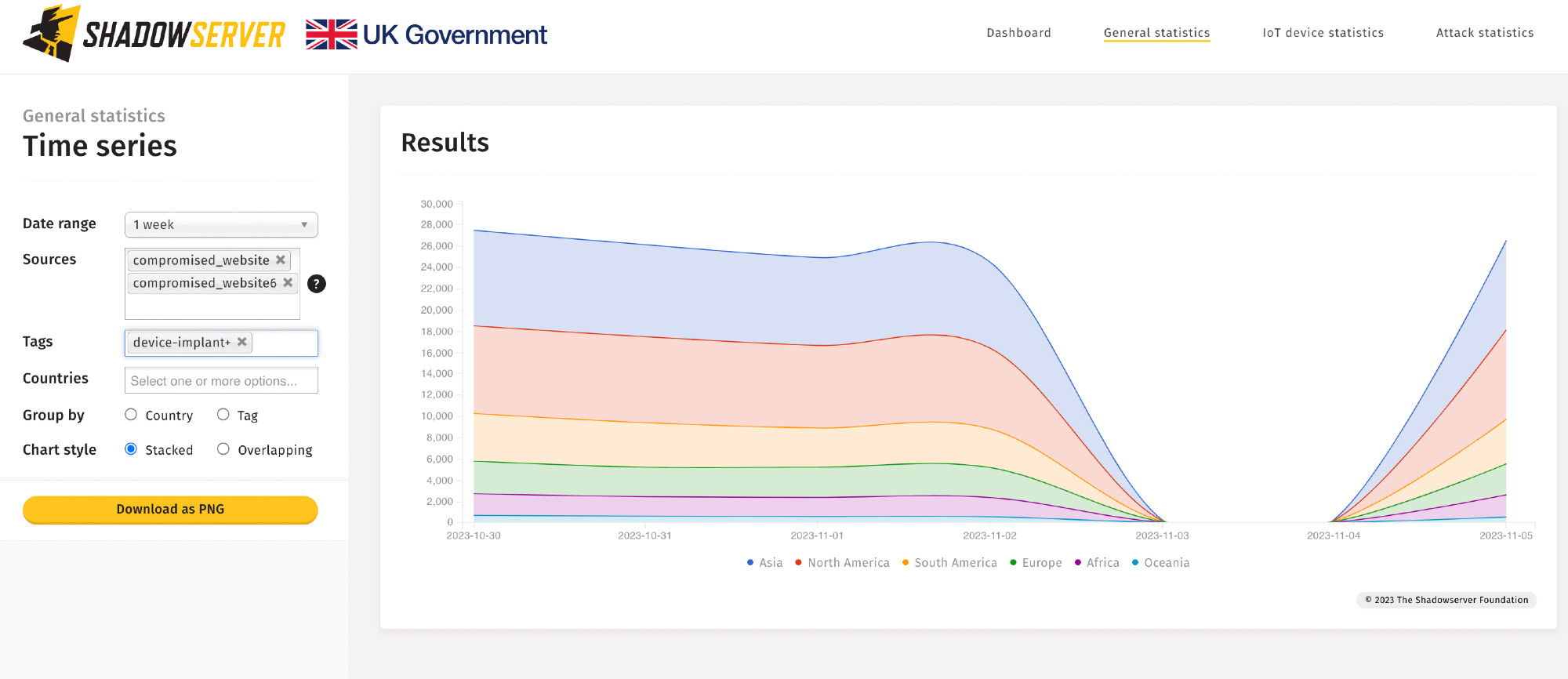
UPDATE: Cisco IOS XE Web UI CVE-2023-20198 version 3 BadCandy implant detection scans up and running (hat tip to LeakIX). Total implant detections at around 26.5K unique IPs. Dashboard tracker: dashboard.shadowserver.org/statistics/c...
Yes, I am not sure how to share that privately however, so I may look at your link tree and ping you separately
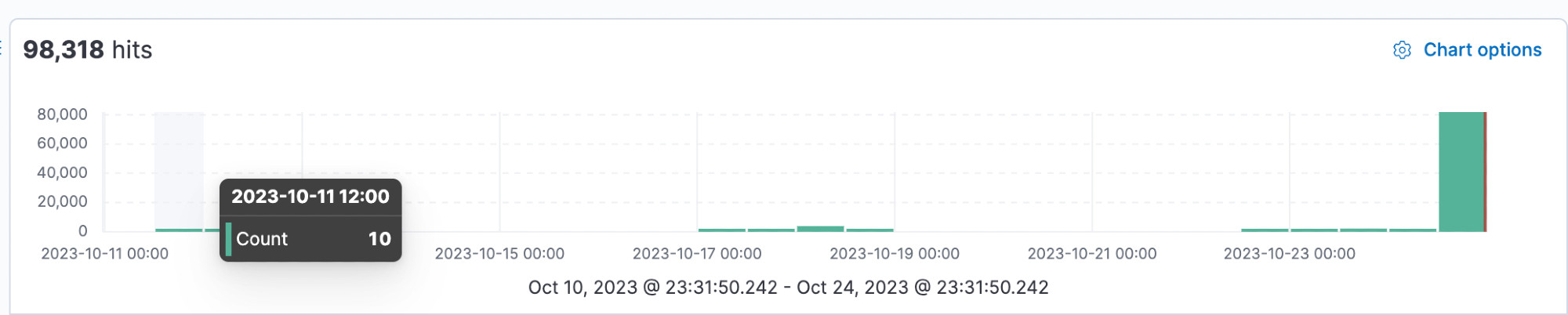
Sharp increase in queries for "/oauth/idp/.well-known/openid-configuration" endpoint associated with Citrix NetScaler CVE-2023-4966 (leaking of session tokens) observed by our honeypot sensors. This is after recent Assetnote assetnote.io/resources/re... publication.
Oh yeah, all of their tools are free.
Welcome to our lives 🙈🫣😣
I’m a big fan of Objective-See’s MacOS security tools. Knockknock is an on demand scanner that finds weird things: objective-see.org/products/kno...objective-see.org/products/blo... Both do require some tech knowledge
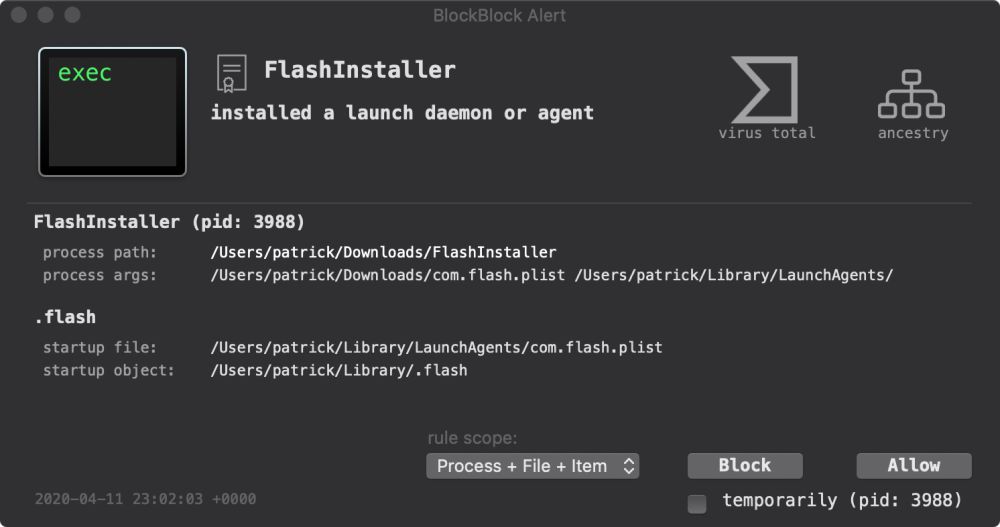
Protection Against Persistent Mac Malware
Hey Frank, sure! I run an infosec feed here in Bluesky (how I found your post) and work in infosec. Would love to hear about this Wordpress attack